Which product correlates logs and detects security threats, providing a centralized display of potential attack patterns from all network devices?
A client has created a new Gateway object that will be managed at a remote location. When the client attempts to install the Security Policy to the new Gateway object, the object does not appear in the Install On check box.
What should you look for?
Vanessa is firewall administrator in her company; her company is using Check Point firewalls on central and remote locations, which are managed centrally by R80 Security Management Server. One central location has an installed R77.30 Gateway on Open server. Remote location is using Check Point UTM-1 570 series appliance with R71. Which encryption is used in Secure Internal Communication (SIC) between central management and firewall on each location?
Which of the following is NOT a valid backup command for a Security Management Server?
What does ExternalZone represent in the presented rule?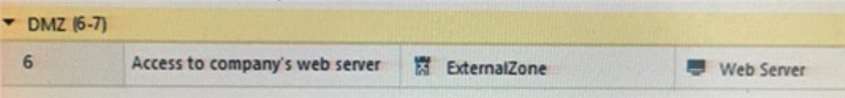
Enter your email address to download CheckPoint.156-215.80.v2022-08-21.q419 Dumps
