What are the two types of address translation rules?
What does ExternalZone represent in the presented rule?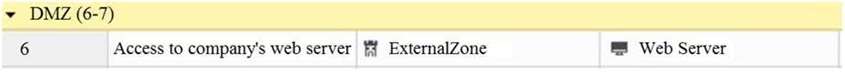
Fill in the blank: The __________ is used to obtain identification and security information about network users.
You want to define a selected administrator's permission to edit a layer. However, when you click the + sign in the "Select additional profile that will be able edit this layer" you do not see anything. What is the most likely cause of this problem?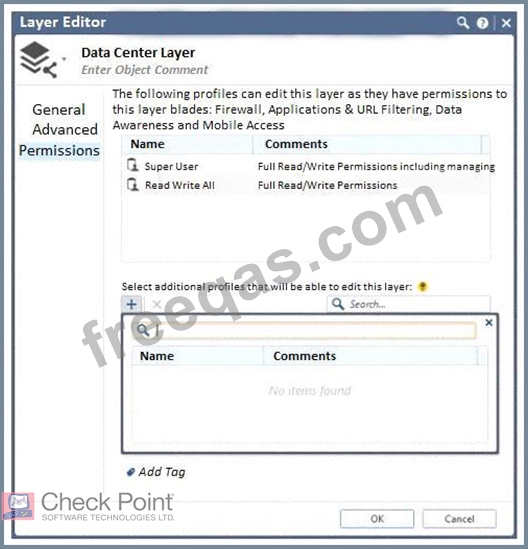
Which Check Point software blade provides visibility of users, groups and machines while also providing access control through identity-based policies?
Enter your email address to download CheckPoint.156-215.80.v2022-08-21.q419 Dumps
