Drag and drop the TCP/IP protocols from the left onto the transmission protocols on the right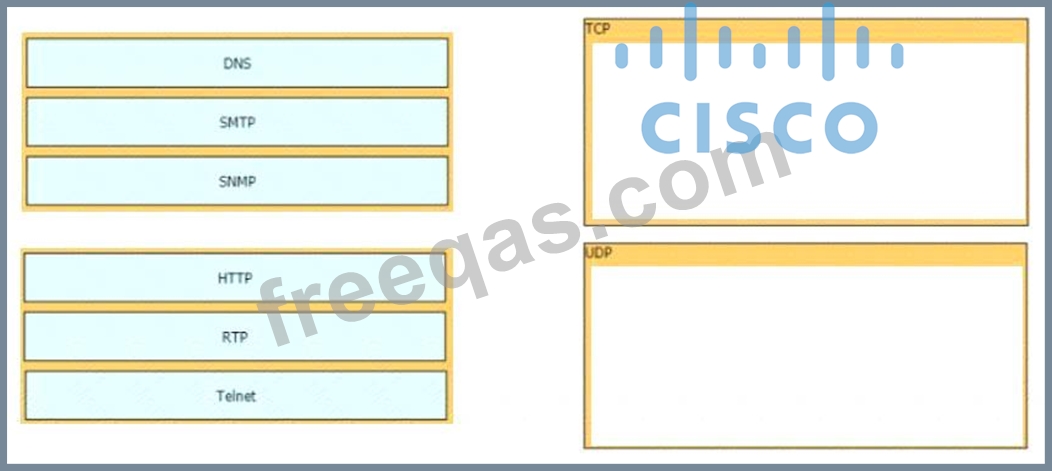
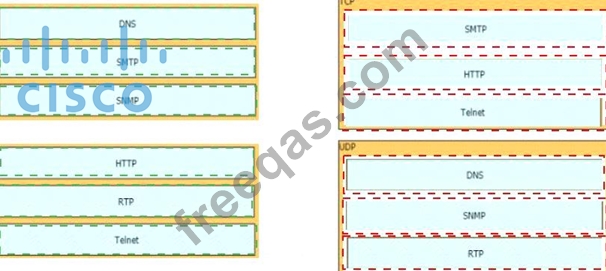

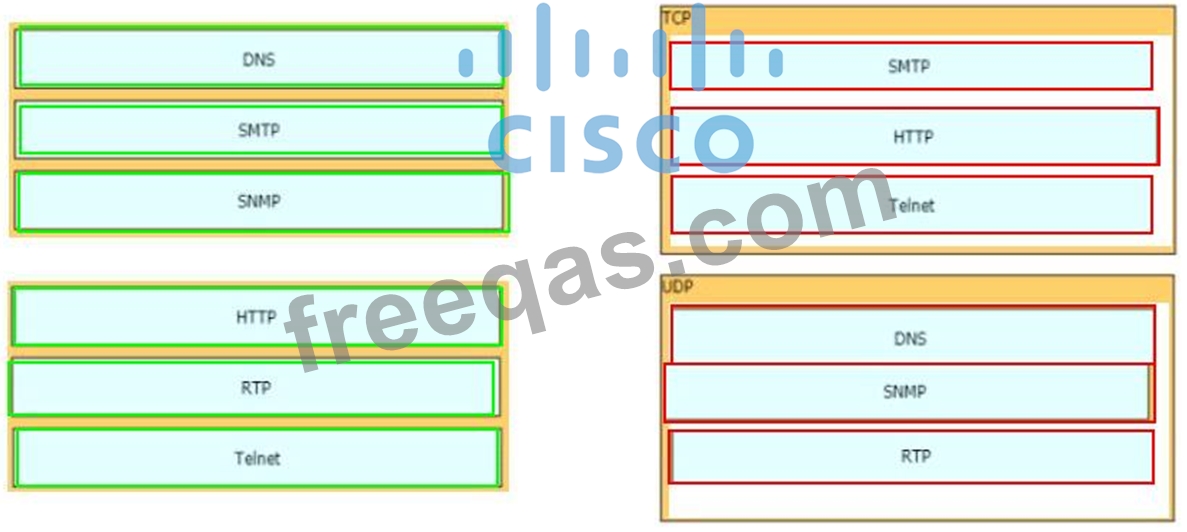
Drag and drop the TCP/IP protocols from the left onto the transmission protocols on the right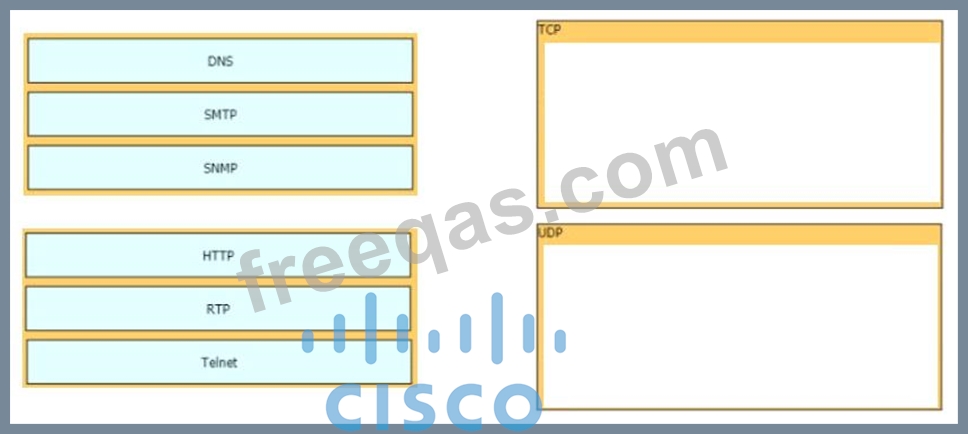
Router R1 must send all traffic without a matching routing-table entry to 192.168.1.1. Which configuration accomplishes this task?
How does machine learning improve the detection of unauthorized network access?
