An attacker exploits the logic validation mechanisms of an e-commerce website. He successfully purchases a product worth $100 for $10 by modifying the URL exchanged between the client and the server.
Original
URL: http://www.buyonline.com/product.aspx?profile=12
&debit=100
Modified URL: http://www.buyonline.com/product.aspx?profile=12
&debit=10
Identify the attack depicted in the above scenario.
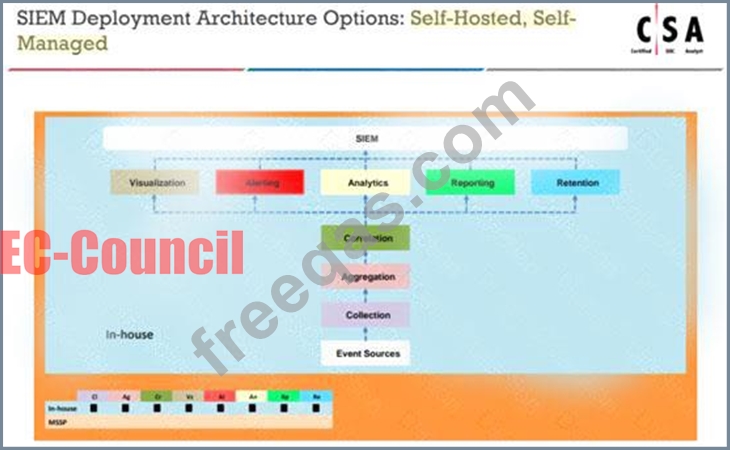
An organization is implementing and deploying the SIEM with following capabilities.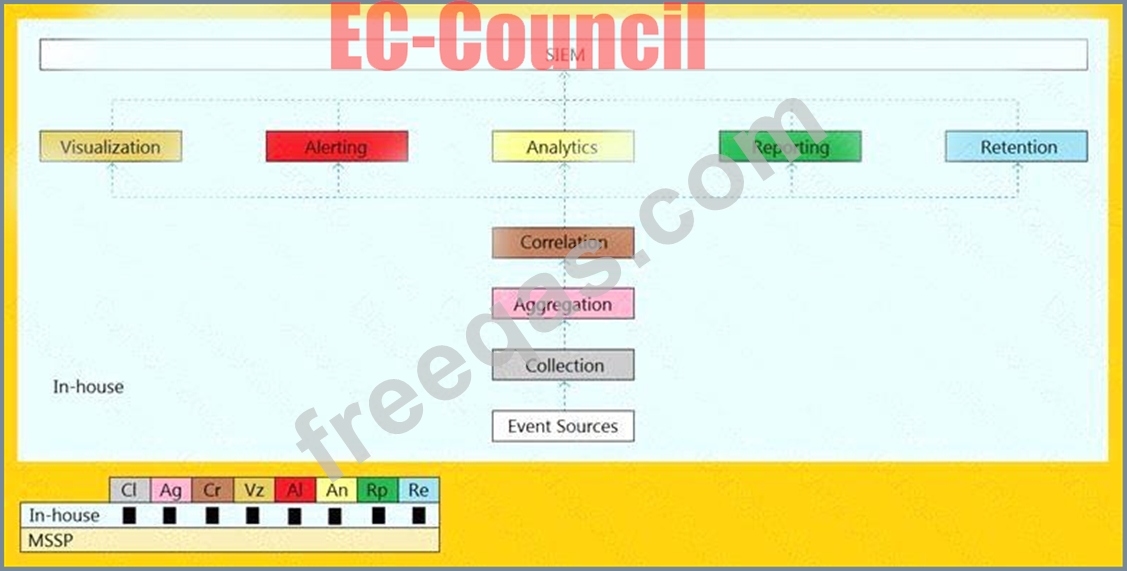
What kind of SIEM deployment architecture the organization is planning to implement?
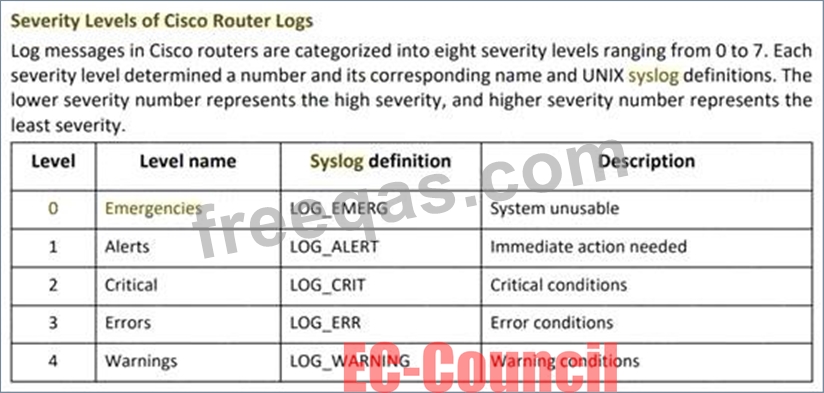
The Syslog message severity levels are labelled from level 0 to level 7.
What does level 0 indicate?
Where will you find the reputation IP database, if you want to monitor traffic from known bad IP reputation using OSSIM SIEM?
