Which three statements explain a flow-based antivirus profile? (Choose three.)
Which three methods can you use to deliver the token code to a user who is configured to use two- factor authentication? (Choose three.)
Refer to the exhibit.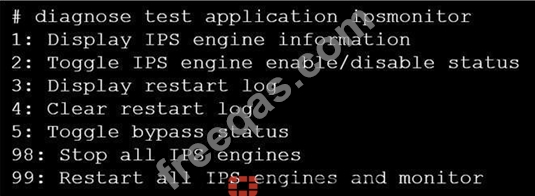
Examine the intrusion prevention system (IPS) diagnostic command.
Which statement is correct If option 5 was used with the IPS diagnostic command and the outcome was a decrease in the CPU usage?
Which method allows management access to the FortiGate CLI without network connectivity?
Which three strategies are valid SD-WAN rule strategies for member selection? (Choose three.)
La respuesta es A,B y C. Manual with load balancing. Best Quality with load balancing. Lowest Cost (SLA) with load balancing. https://Estrategia de mejor calidad en FortiOS 7.4.4
Enter your email address to download Fortinet.FCP_FGT_AD-7.4.v2024-12-12.q52 Dumps
