Which statement is correct regarding the inspection of some of the services available by web applications embedded in third-party websites?
Refer to the exhibit showing a debug flow output.
Which two statements about the debug flow output are correct? (Choose two.)
Refer to the exhibit.
The exhibit shows proxy policies and proxy addresses, the authentication rule and authentication scheme, users, and firewall address.
An explicit web proxy is configured for subnet range 10.0.1.0/24 with three explicit web proxy policies.
The authentication rule is configured to authenticate HTTP requests for subnet range 10.0.1.0/24 with a form-based authentication scheme for the FortiGate local user database. Users will be prompted for authentication.
How will FortiGate process the traffic when the HTTP request comes from a machine with the source IP 10.0.1.10 to the destination http://www.fortinet.com? (Choose two.)
Refer to the exhibit.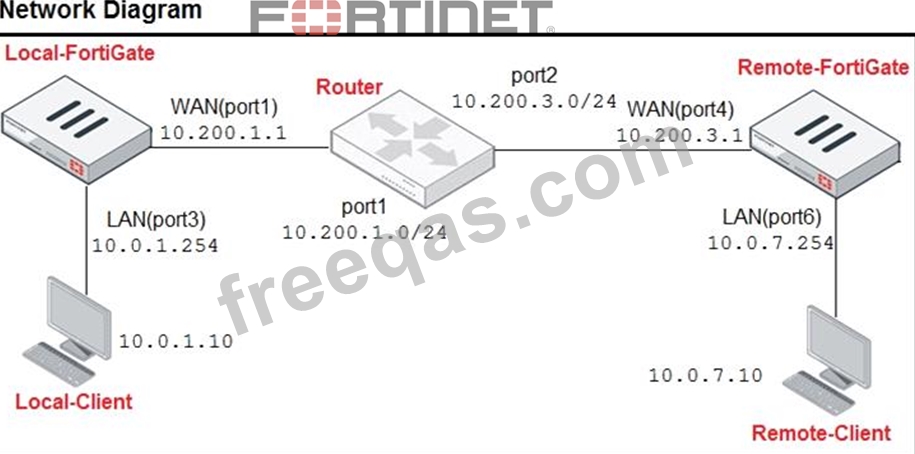
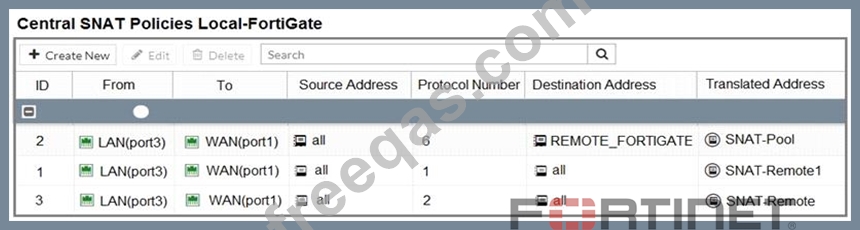
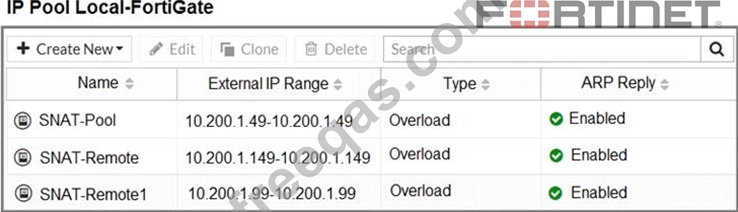
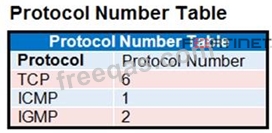
The exhibit contains a network diagram, central SNAT policy, and IP pool configuration.
The WAN (port1) interface has the IP address 10.200.1.1/24.
The LAN (port3) interface has the IP address 10.0.1.254/24.
A firewall policy is configured to allow to destinations from LAN (port3) to WAN (port1).
Central NAT is enabled, so NAT settings from matching Central SNAT policies will be applied.
Which IP address will be used to source NAT the traffic, if the user on Local-Client (10.0.1.10) pings the IP address of Remote-FortiGate (10.200.3.1)?
Examine this PAC file configuration.
Which of the following statements are true? (Choose two.)
Enter your email address to download Fortinet.NSE4_FGT-7.0.v2022-10-06.q63 Dumps
