Which of the following descriptions are correct about the buffer overflow attack? (Multiple Choice)
The process of electronic forensics includes: protecting the site, obtaining evidence, preserving evidence, identifying evidence, analyzing evidence, tracking and presenting evidence.
The scene of internal users access the internet as shown, the subscriber line process are:
1. After authentication, USG allow the connection
2. The user input http://1.1.1.1 to access Internet
3. USG push authentication interface, User =? Password =?
4. The user successfully accessed http://1.1.1.1, equipment create Session table.
5. User input User = *** Password = ***
Which the following procedure is correct?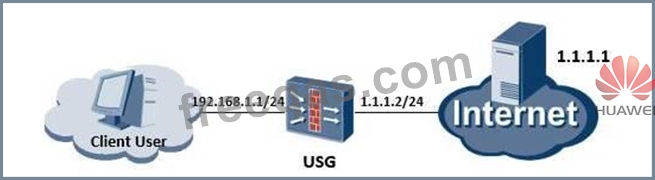
Digital signatures are used to generate digital fingerprints by using a hashing algorithm to ensure the integrity of data transmission
