Which of the following options are supported by VPN technology to encrypt data messages? (Multiple choice)
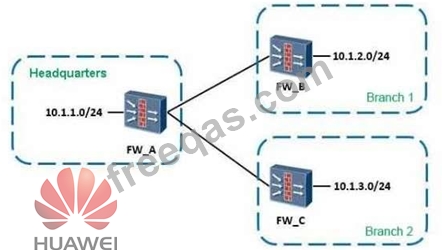
As shown, when configuring the point-to-multipoint scenarios, the headquarters network segment is
10.1.1.0/24, the segment of branch 1 is 10.1.2.0/24, of branch 2 is 10.1.3.0/24.
About the protected data flow configuration which defined by headquarters and branch offices, which of the following combinations can be the full matched requirements?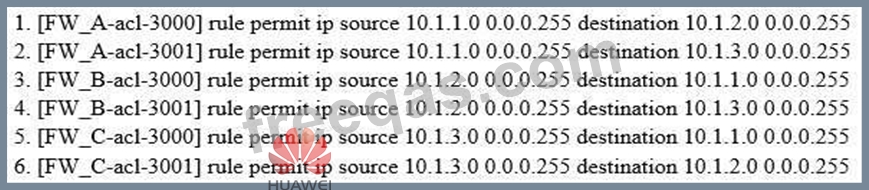
In order to obtain evidence of crime, it is necessary to master the technology of intrusion tracking. Which of the following descriptions are correct about the tracking technology? (Multiple Choice)
Which of the following is wrong about the management of Internet users?
