Which of the following is an action to be taken during the summary phase of the cybersecurity emergency response? (Multiple Choice)
The following security policy command, representatives of the meaning: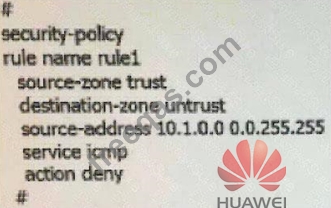
Which of the following protocols can guarantee the confidentiality of data transmission? (Multiple Choice)
Which of the following is not part of the method used in the Detection section of the P2DR model?
Which of the following are the same features of Windows and LINUX systems? (MultipleChoice)
