The following description of investigation and evidence collection, which one is correct
Database operation records can be used as ___ evidence to backtrack security events.[fill in the blank]*
Please classify the following security defenses into the correct classification.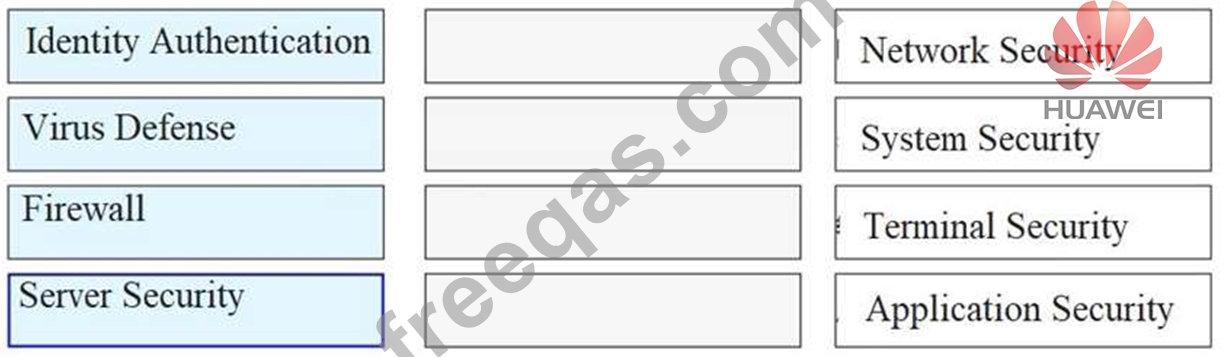

During the process of establishing IPSec VPN between peers FW_A and FW_B, two types of security associations need to be established in two stages. In the first stage, _____ is established to verify the identity of the peers.[fill in the blank]*
The shard cache technology will wait for the arrival of the first shard packet, and then reassemble and decrypt all the packets, and then do subsequent processing by the device to ensure that the session can proceed normally in some application scenarios.
Enter your email address to download Huawei.H12-711_V4.0.v2024-03-30.q30 Dumps
