The following figure shows the configuration of the URL filtering configuration file. Regarding the configuration, which of the following statements is correct?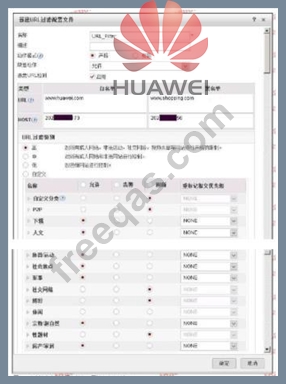
To protect the security of data transmission, more and more websites or companies choose to encrypt traffic through SSL.
Which of the following statements is true about the threat detection of SSL traffic using Huawei NIP6000?
For SYIN Flood attacks, TCP source authentication and TCP proxy can be used for defense. Which of the following descriptions is correct?
Which of the following is correct about enhanced mode in HTTP Flood Source authentication? (Multiple selection)
The anti-virus feature configured on the Huawei USG6000 product does not take effect. Which of the following are the possible reasons? (multiple choice)
Enter your email address to download Huawei.H12-722-ENU.v2022-04-19.q106 Dumps
