Which of the following is the GREATEST advantage of application penetration testing over vulnerability
scanning?
An information security manager has identified and implemented migrating controls according to industry best practices. Which of the following is the GREATEST risk associated with this approach?
E-mail traffic from the Internet is routed via firewall-1 to the mail gateway. Mail is routed from the mail gateway, via firewall-2, to the mail recipients in the internal network. Other traffic is not allowed. For example, the firewalls do not allow direct traffic from the Internet to the internal network.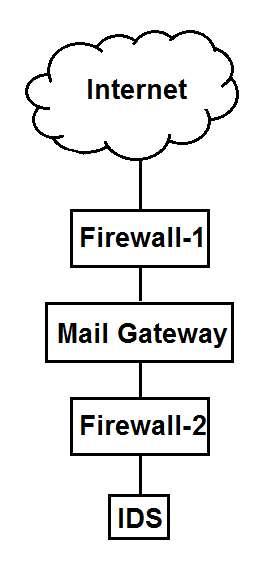
The intrusion detection system (IDS) detects traffic for the internal network that did not originate from the mail gateway. The FIRST action triggered by the IDS should be to:
.What kind of testing should programmers perform following any changes to an application or system?
Which of the following is the BEST method for converting a file into a format suitable for data analysis in a forensic investigation?
