Once an organization has finished the business process reengineering (BPR) of all its critical operations, an IS auditor would MOST likely focus on a review of:
In the context of physical access control, what is known as the process of verifying user identities?
E-mail traffic from the Internet is routed via firewall-1 to the mail gateway. Mail is routed from the mail gateway, via firewall-2, to the mail recipients in the internal network. Other traffic is not allowed. For example, the firewalls do not allow direct traffic from the Internet to the internal network.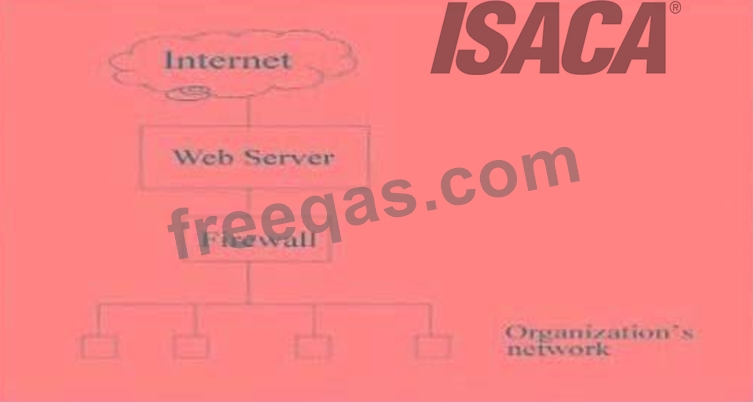
The intrusion detection system (IDS) detects traffic for the internal network that did not originate from the mail gateway. The FIRST action triggered by the IDS should be to:
Which of the following is the FIRST step in initiating a data classification program?
Which of the following is an IS auditor's BEST course of action upon learning that preventive controls have been replaced with detective and corrective controls'
