Which of the following observations should be of GREATEST concern to an IS auditor reviewing a large organization's virtualization environment?
in a controlled application development environment, the MOST important segregation of duties should be between the person who implements changes into the production environment and the:
Creating which of the following is how a hacker can insure his ability to return to the hacked system at will?
Assuming this diagram represents an internal facility and the organization is implementing a firewall protection program, where should firewalls be installed?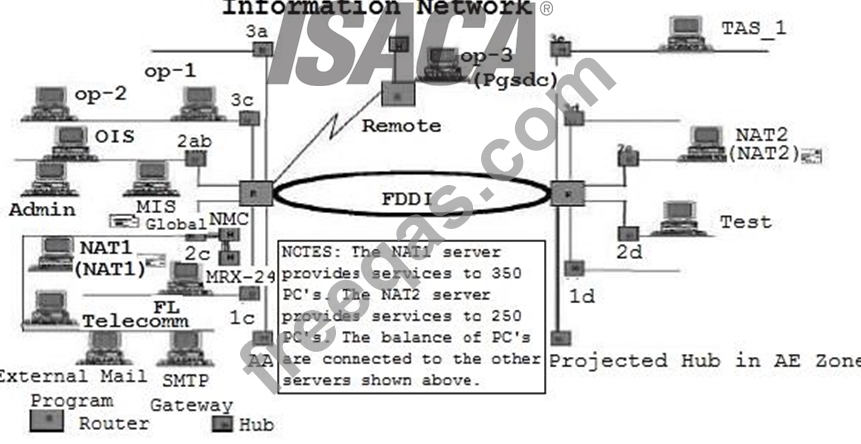
An IS auditor reviewing wireless network security determines that the Dynamic Host Configuration Protocol is disabled at all wireless access points. This practice:
