Section: Information System Acquisition, Development and Implementation
Explanation/Reference:
For your exam you should know below information about agile development:
Agile software development is a group of software development methods based on iterative and
incremental development, where requirements and solutions evolve through collaboration between self-
organizing, cross-functional teams. It promotes adaptive planning, evolutionary development and delivery, a
time-boxed iterative approach, and encourages rapid and flexible response to change. It is a conceptual
framework that promotes foreseen tight iterations throughout the development cycle.
Agile Development
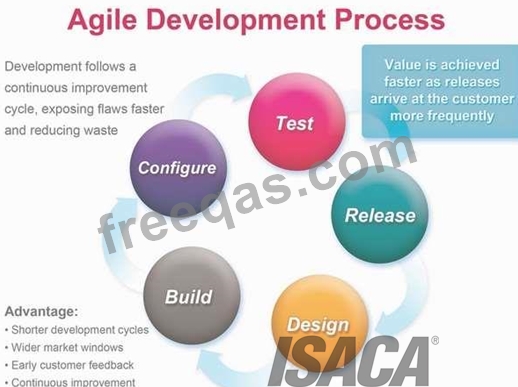
The Agile Manifesto introduced the term in 2001. Since then, the Agile Movement, with all its values,
principles, methods, practices, tools, champions and practitioners, philosophies and cultures, has
significantly changed the landscape of the modern software engineering and commercial software
development in the Internet era.
Agile principles
The Agile Manifesto is based on twelve principles:
Customer satisfaction by rapid delivery of useful software
Welcome changing requirements, even late in development
Working software is delivered frequently (weeks rather than months)
Close, daily cooperation between business people and developers
Projects are built around motivated individuals, who should be trusted
Face-to-face conversation is the best form of communication (co-location)
Working software is the principal measure of progress
Sustainable development, able to maintain a constant pace
Continuous attention to technical excellence and good design
Simplicity-the art of maximizing the amount of work not done-is essential
Self-organizing teams
Regular adaptation to changing circumstances
What is Scrum?
Scrum is the most popular way of introducing Agility due to its simplicity and flexibility. Because of this
popularity, many organizations claim to be "doing Scrum" but aren't doing anything close to Scrum's actual
definition. Scrum emphasizes empirical feedback, team self-management, and striving to build properly
tested product increments within short iterations. Doing Scrum as it's actually defined usually comes into
conflict with existing habits at established non-Agile organizations.
The following were incorrect answers:
Software prototyping- Software prototyping, refers to the activity of creating prototypes of software
applications, i.e., incomplete versions of the software program being developed. It is an activity that can
occur in software development and is comparable to prototyping as known from other fields, such as
mechanical engineering or manufacturing.
Rapid application development (RAD) is a software development methodology that uses minimal planning
in favor of rapid prototyping. The "planning" of software developed using RAD is interleaved with writing the
software itself. The lack of extensive per-planning generally allows software to be written much faster, and
makes it easier to change requirements.
Component Based Development - It is a reuse-based approach to defining, implementing and composing
loosely coupled independent components into systems. This practice aims to bring about an equally wide-
ranging degree of benefits in both the short-term and the long-term for the software itself and for
organizations that sponsor such software.
The following reference(s) were/was used to create this question:
CISA review manual 2014 Page number 194

