Section: Information System Operations, Maintenance and Support
Explanation/Reference:
Network database model-The network model expands upon the hierarchical structure, allowing many-to-
many relationships in a tree-like structure that allows multiple parents.
For your exam you should know below information about database models:
A database model is a type of data model that determines the logical structure of a database and
fundamentally determines in which manner data can be stored, organized, and manipulated. The most
popular example of a database model is the relational model, which uses a table-based format.
Common logical data models for databases include:
Hierarchical database model
Network model
Relational model
Object-relational database models
Hierarchical database model
In a hierarchical model, data is organized into a tree-like structure, implying a single parent for each record.
A sort field keeps sibling records in a particular order. Hierarchical structures were widely used in the early
mainframe database management systems, such as the Information Management System (IMS) by IBM,
and now describe the structure of XML documents. This structure allows one one-to-many relationship
between two types of data. This structure is very efficient to describe many relationships in the real world;
recipes, table of contents, ordering of paragraphs/verses, any nested and sorted information.
This hierarchy is used as the physical order of records in storage. Record access is done by navigating
through the data structure using pointers combined with sequential accessing. Because of this, the
hierarchical structure is inefficient for certain database operations when a full path (as opposed to upward
link and sort field) is not also included for each record. Such limitations have been compensated for in later
IMS versions by additional logical hierarchies imposed on the base physical hierarchy.
Hierarchical database model
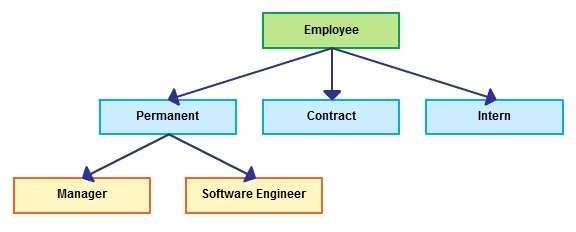
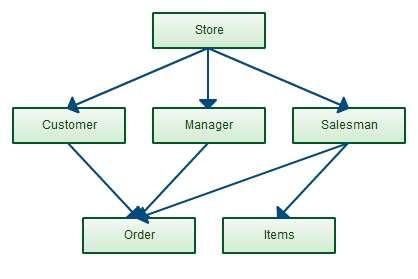
Network database model
The network model expands upon the hierarchical structure, allowing many-to-many relationships in a
tree-like structure that allows multiple parents. It was the most popular before being replaced by the
relational model, and is defined by the CODASYL specification.
The network model organizes data using two fundamental concepts, called records and sets. Records
contain fields (which may be organized hierarchically, as in the programming language COBOL). Sets (not
to be confused with mathematical sets) define one-to-many[disambiguation needed] relationships between
records: one owner, many members. A record may be an owner in any number of sets, and a member in
any number of sets.
A set consists of circular linked lists where one record type, the set owner or parent, appears once in each
circle, and a second record type, the subordinate or child, may appear multiple times in each circle. In this
way a hierarchy may be established between any two record types, e.g., type A is the owner of
B. At the
same time another set may be defined where B is the owner of
A. Thus all the sets comprise a general
directed graph (ownership defines a direction), or network construct. Access to records is either sequential
(usually in each record type) or by navigation in the circular linked lists.
The network model is able to represent redundancy in data more efficiently than in the hierarchical model,
and there can be more than one path from an ancestor node to a descendant. The operations of the
network model are navigational in style: a program maintains a current position, and navigates from one
record to another by following the relationships in which the record participates. Records can also be
located by supplying key values.
Network Database model
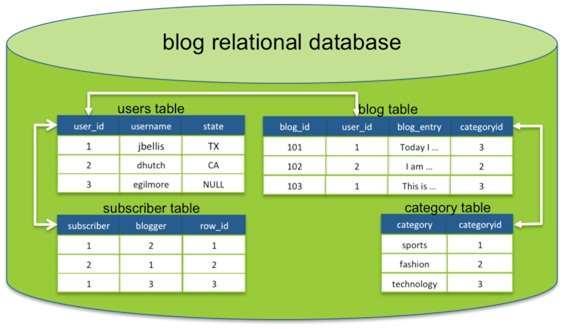
Relational database model
In the relational model of a database, all data is represented in terms of tulles, grouped into relations. A
database organized in terms of the relational model is a relational database.
In the relational model, related records are linked together with a "key".
The purpose of the relational model is to provide a declarative method for specifying data and queries:
users directly state what information the database contains and what information they want from it, and let
the database management system software take care of describing data structures for storing the data and
retrieval procedures for answering queries.
Most relational databases use the SQL data definition and query language; these systems implement what
can be regarded as an engineering approximation to the relational model. A table in an SQL database
schema corresponds to a predicate variable; the contents of a table to a relation; key constraints, other
constraints, and SQL queries correspond to predicates. However, SQL databases, including DB2, deviate
from the relational model in many details, and Cod fiercely argued against deviations that compromise the
original principles.
Relational database model
Object-relational database Model
An object-relational database (ORD), or object-relational database management system (ORDBMS), is a
database management system (DBMS) similar to a relational database, but with an object-oriented
database model: objects, classes and inheritance are directly supported in database schemas and in the
query language. In addition, just as with pure relational systems, it supports extension of the data model
with custom data-types and methods.
Example of an object-oriented database model
An object-relational database can be said to provide a middle ground between relational databases and
object-oriented databases (OODBMS). In object-relational databases, the approach is essentially that of
relational databases: the data resides in the database and is manipulated collectively with queries in a
query language; at the other extreme are OODBMSes in which the database is essentially a persistent
object store for software written in an object-oriented programming language, with a programming API for
storing and retrieving objects, and little or no specific support for querying.
The following were incorrect answers:
Hierarchical database model - In a hierarchical model, data is organized into a tree-like structure, implying
a single parent for each record. A sort field keeps sibling records in a particular order.
Relational model- In the relational model of a database, all data is represented in terms of tulles, grouped
into relations. A database organized in terms of the relational model is a relational database. In the
relational model, related records are linked together with a "key".
Object-relational database models- An object-relational database can be said to provide a middle ground
between relational databases and object-oriented databases (OODBMS). In object-relational databases,
the approach is essentially that of relational databases: the data resides in the database and is manipulated
collectively with queries in a query language; at the other extreme are OODBMSes in which the database is
essentially a persistent object store for software written in an object-oriented programming language, with a
programming API for storing and retrieving objects, and little or no specific support for querying.
The following reference(s) were/was used to create this question:
CISA review manual 2014 Page number 254



