When classifying information, it is MOST important to align the classification to:
Which of the following would minimize the risk of losing transactions as a result of a disaster?
A call-back system requires that a user with an id and password call a remote server through a dial-up line, then the server disconnects and:
The editing/validation of data entered at a remote site would be performed MOST effectively at the:
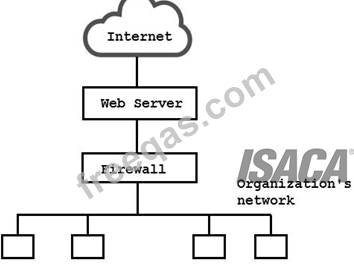
To detect attack attempts that the firewall is unable to recognize, an IS auditor should recommend placing a network intrusion detection system (IDS) between the: