Which of the following encryption methods uses a matching pair of key-codes, securely distributed, which are used once-and-only-once to encode and decode a single message?
E-mail traffic from the Internet is routed via firewall-1 to the mail gateway. Mail is routed from the mail gateway, via firewall-2, to the mail recipients in the internal network. Other traffic is not allowed. For example, the firewalls do not allow direct traffic from the Internet to the internal network.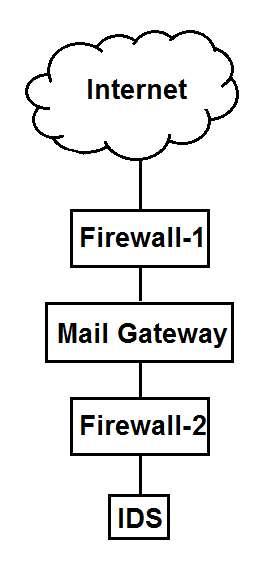
The intrusion detection system (IDS) detects traffic for the internal network that did not originate from the mail gateway. The FIRST action triggered by the IDS should be to:
Which of the following is the MOST important benefit of Involving IS audit when implementing governance of enterprise IT?
Total billing amounts on invoices are automatically transferred to an organization's account ledger weekly.
During an IS audit, the auditor discovers that one week's billing is missing from the ledger. Which of the following areas should the auditor examine FIRST?
An organization has an acceptable use policy in place, but users do not formally acknowledge the policy.
Which of the following is the MOST significant risk from this finding?
