Section: Information System Operations, Maintenance and Support
Explanation/Reference:
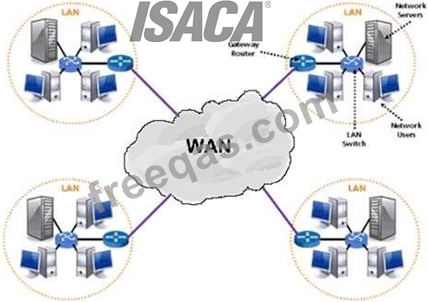
A wide area network (WAN) is a network that covers a broad area (i.e., any telecommunications network
that links across metropolitan, regional, national or international boundaries) using leased
telecommunication lines.
For your exam you should know below information about computer networks:
Local Area Network (LAN)
A local area network (LAN) is a computer network that interconnects computers within a limited area such
as a home, school, computer laboratory, or office building using network media.
Local Area Network

Wide Area Network
A wide area network (WAN) is a network that covers a broad area (i.e., any telecommunications network
that links across metropolitan, regional, national or international boundaries) using leased
telecommunication lines.
Wide Area Network
Metropolitan Area Network
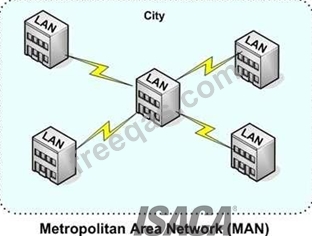
A metropolitan area network (MAN) is a computer network in which two or more computers or
communicating devices or networks which are geographically separated but in same metropolitan city and
are connected to each other are said to be connected on MAN. Metropolitan limits are determined by local
municipal corporations; the larger the city, the bigger the MAN, the smaller a metro city, smaller the MAN
Metropolitan Area Network
Personal Area Network
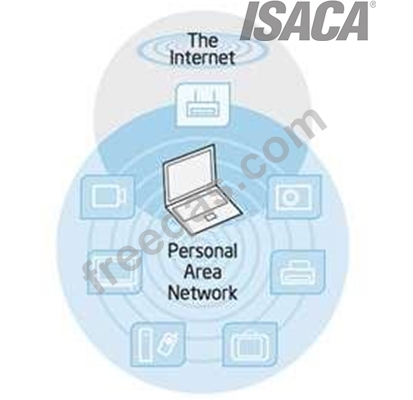
A personal area network (PAN) is a computer network used for data transmission among devices such as
computers, telephones and personal digital assistants. PANs can be used for communication among the
personal devices themselves (intrapersonal communication), or for connecting to a higher level network
and the Internet (an uplink).
Personal Area Network
Storage Area Network
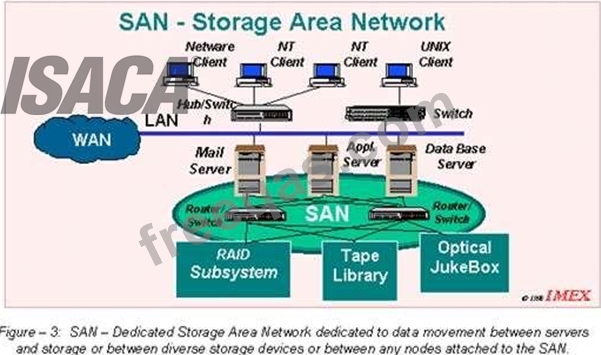
A storage area network (SAN) is a dedicated network that provides access to consolidated, block level data
storage. SANs are primarily used to enhance storage devices, such as disk arrays, tape libraries, and
optical jukeboxes, accessible to servers so that the devices appear like locally attached devices to the
operating system. A SAN typically has its own network of storage devices that are generally not accessible
through the local area network (LAN) by other devices.
Storage Area Network
The following were incorrect answers:
PAN - A personal area network (PAN) is a computer network used for data transmission among devices
such as computers, telephones and personal digital assistants. PANs can be used for communication
among the personal devices themselves (intrapersonal communication), or for connecting to a higher level
network and the Internet (an uplink).
LAN - A local area network (LAN) is a computer network that interconnects computers within a limited area
such as a home, school, computer laboratory, or office building using network media.
SAN - A storage area network (SAN) is a dedicated network that provides access to consolidated, block
level data storage. SANs are primarily used to enhance storage devices, such as disk arrays, tape libraries,
and optical jukeboxes, accessible to servers so that the devices appear like locally attached devices to the
operating system. A SAN typically has its own network of storage devices that are generally not accessible
through the local area network (LAN) by other devices.
The following reference(s) were/was used to create this question:
CISA review manual 2014 Page number 258





