Section: Information System Operations, Maintenance and Support
Explanation/Reference:
The INCORRECTLY keyword is used in the question. You need to find out a statement which is not valid
about router. Router builds a routing table based on IP address and not on MAC address.
Difference between Router and Bridge:
Router
Bridge
Creates a new header for each packet
Does not alter header. Only reads the header
Builds routing table based on IP address
Build forwarding table based on MAC address
Assigns a different network address per port
Use the same network address for all ports
Filters traffic based on IP address
Filter traffic based on MAC address
Does not forward broadcast packet
Forward broadcast packet
Does not forward traffic that contain destination address unknown to the router
Forward traffic if destination address is unknown to bridge
For your exam you should know below information about network devices:
Repeaters
A repeater provides the simplest type of connectivity, because it only repeats electrical signals between
cable segments, which enables it to extend a network. Repeaters work at the physical layer and are add-on
devices for extending a network connection over a greater distance. The device amplifies signals because
signals attenuate the farther they have to travel.
Repeaters can also work as line conditioners by actually cleaning up the signals. This works much better
when amplifying digital signals than when amplifying analog signals, because digital signals are discrete
units, which makes extraction of background noise from them much easier for the amplifier. If the device is
amplifying analog signals, any accompanying noise often is amplified as well, which may further distort the
signal.
A hub is a multi-port repeater. A hub is often referred to as a concentrator because it is the physical
communication device that allows several computers and devices to communicate with each other. A hub
does not understand or work with IP or MAC addresses. When one system sends a signal to go to another
system connected to it, the signal is broadcast to all the ports, and thus to all the systems connected to the
concentrator.
Repeater

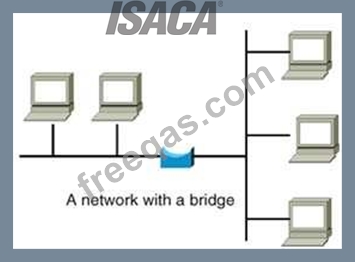
Bridges
A bridge is a LAN device used to connect LAN segments. It works at the data link layer and therefore works
with MAC addresses. A repeater does not work with addresses; it just forwards all signals it receives.
When a frame arrives at a bridge, the bridge determines whether or not the MAC address is on the local
network segment. If the MAC address is not on the local network segment, the bridge forwards the frame
to the necessary network segment.
Bridge
Routers
Routers are layer 3, or network layer, devices that are used to connect similar or different networks. (For
example, they can connect two Ethernet LANs or an Ethernet LAN to a Token Ring LAN.) A router is a
device that has two or more interfaces and a routing table so it knows how to get packets to their
destinations. It can filter traffic based on access control lists (ACLs), and it fragments packets when
necessary. Because routers have more network-level knowledge, they can perform higher-level functions,
such as calculating the shortest and most economical path between the sending and receiving hosts.
Router and Switch

Switches
Switches combine the functionality of a repeater and the functionality of a bridge. A switch amplifies the
electrical signal, like a repeater, and has the built-in circuitry and intelligence of a bridge. It is a multi-port
connection device that provides connections for individual computers or other hubs and switches.
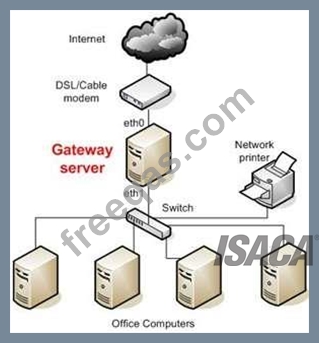
Gateways
Gateway is a general term for software running on a device that connects two different environments and
that many times acts as a translator for them or somehow restricts their interactions.
Usually a gateway is needed when one environment speaks a different language, meaning it uses a certain
protocol that the other environment does not understand. The gateway can translate Internetwork Packet
Exchange (IPX) protocol packets to IP packets, accept mail from one type of mail server and format it so
another type of mail server can accept and understand it, or connect and translate different data link
technologies such as FDDI to Ethernet.
Gateway Server
The following were incorrect answers:
The other options presented correctly describes about Router.
The following reference(s) were/was used to create this question:
CISA review manual 2014 Page number 263




