You are asked to re-purpose a NetApp FAS cluster. You need to verify that all encrypted data has been securely erased.
Which two features would allow you to securely re-purpose the array? (Choose two.)
Click the Exhibit button.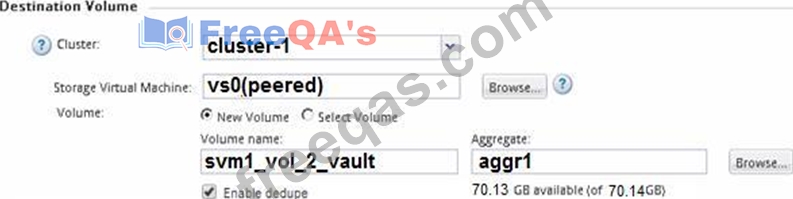
An employee's computer and mapped home folder has been encrypted with ransomware. You are asked to restore the data from a SnapVault repository.
Referring to the exhibit, what happens when the volume is restored?
When you configure a SnapLock feature, where should the ComplianceClock be initialized?
A customer has just purchased a new 2-node AFF A220 cluster running ONTAP 9.7 and moved the older 4- node FAS2650 cluster running ONTAP 9.5 to an off-site location. They want to configure replication to the FAS2650 cluster for both disaster recovery and long-term archiving.
In thisscenario, how would the customer accomplish this task?
A customer wants to set up an SVM DR relationship to protect a source SVM that is dedicated for NAS file services. The source and destination clusters are running ONTAP 9.5.
In this scenario, which application accomplishes this task?
Enter your email address to download NetworkAppliance.NS0-527.v2022-05-18.q55 Dumps
