Give this compartment structure: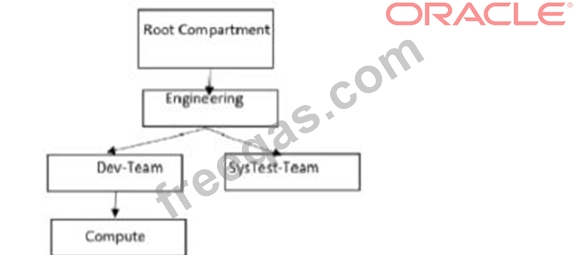
You want to move a compute instance that is in 'Compute' compartment to 'SysTes-Team'.
You login to your Oracle Cloud Infrastructure (OCI)account and use the 'Move Resource' option.
What will happen when you attempt moving the compute resource?
Your security team has informed you that there are a number of malicious requests for your web application coming from a set of IP addresses originating from a country in Europe.
Which of the following methods can be used to mitigate these type of unauthorized requests?
A civil engineering company is running an online portal In which engineers can upload there constructions photos, videos, and other digital files.
There is a new requirement for you to implement: the online portal must offload the digital content to an Object Storage bucket for a period of 72 hours. After the provided time limit has elapsed, the portal will hold all the digital content locally and wait for the next offload period.
Which option fulfills this requirement?
You are designing the network infrastructure for two application servers: appserver-1 and appserver-2 running in two different subnets inside the same Virtual Cloud Network (VCN) Oracle Cloud Infrastructure (OCI). You have a requirement where your end users will access appserver-1 from the internet and appserver-2 from the on-premises network. The on-premises network is connected to your VCN over a FastConnect virtual circuit.
How should you design your routing configuration to meet these requirements?
You work for a German company as the Lead Oracle Cloud Infrastructure architect. You have designed a highly scalable architecture for your company's business critical application which uses the Load Balancer service auto which uses the Load Balancer service, autoscaling configuration for the application servers and a 2 Node VM Oracle RAC database. During the peak utilization period of the- application yon notice that the application is running slow and customers are complaining. This is resulting in support tickets being created for API timeouts and negative sentiment from the customer base.
What are two possible reasons for this application slowness?
