Based on the show security policy rule would match all FTP traffic from the inside zone to the outside zone?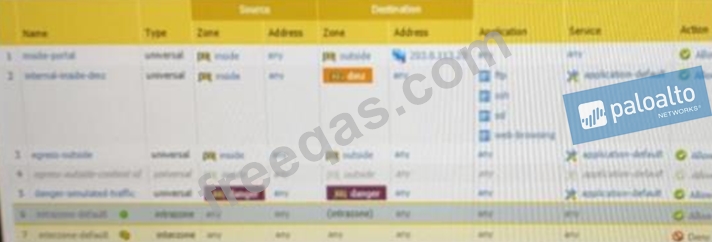
What is considered best practice with regards to committing configuration changes?
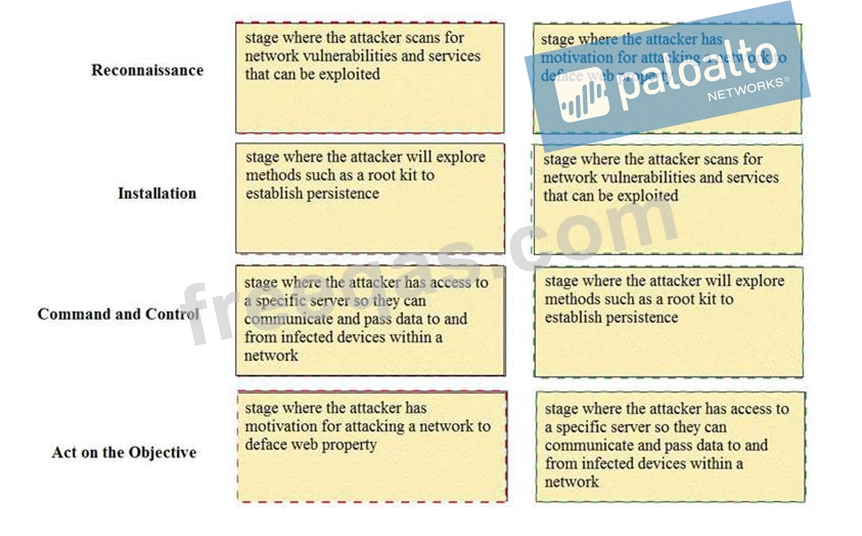
Match the Cyber-Attack Lifecycle stage to its correct description.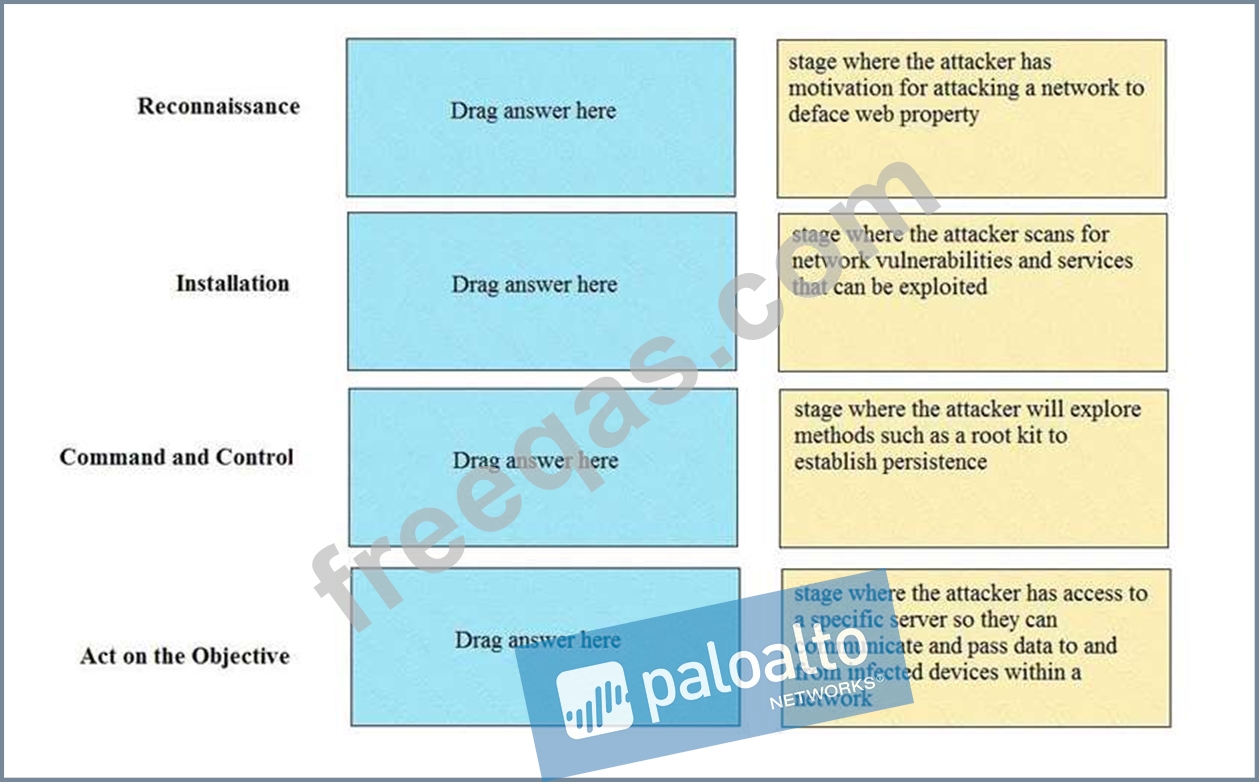
The CFO found a USB drive in the parking lot and decide to plug it into their corporate laptop. The USB drive had malware on it that loaded onto their computer and then contacted a known command and control (CnC) server, which ordered the infected machine to begin Exfiltrating data from the laptop.
Which security profile feature could have been used to prevent the communication with the CnC server?
Given the image, which two options are true about the Security policy rules. (Choose two.)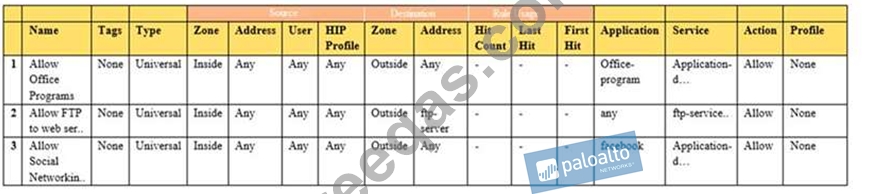
Enter your email address to download PaloAltoNetworks.PCNSA.v2022-04-11.q158 Dumps
