Which feature would be useful for preventing traffic from hosting providers that place few restrictions on content, whose services are frequently used by attackers to distribute illegal or unethical material?
Order the steps needed to create a new security zone with a Palo Alto Networks firewall.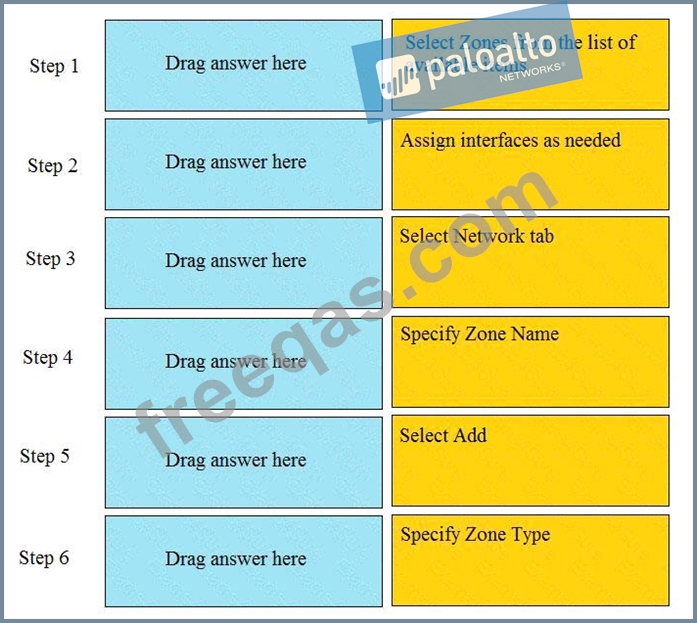

Which path in PAN-OS 10.0 displays the list of port-based security policy rules?
Refer to the exhibit. A web server in the DMZ is being mapped to a public address through DNAT.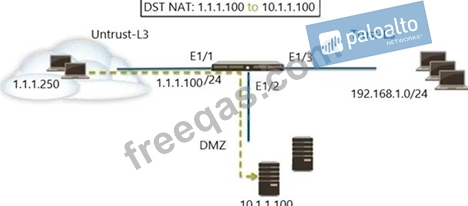
Which Security policy rule will allow traffic to flow to the web server?
An administrator is reviewing the Security policy rules shown in the screenshot below.
Which statement is correct about the information displayed?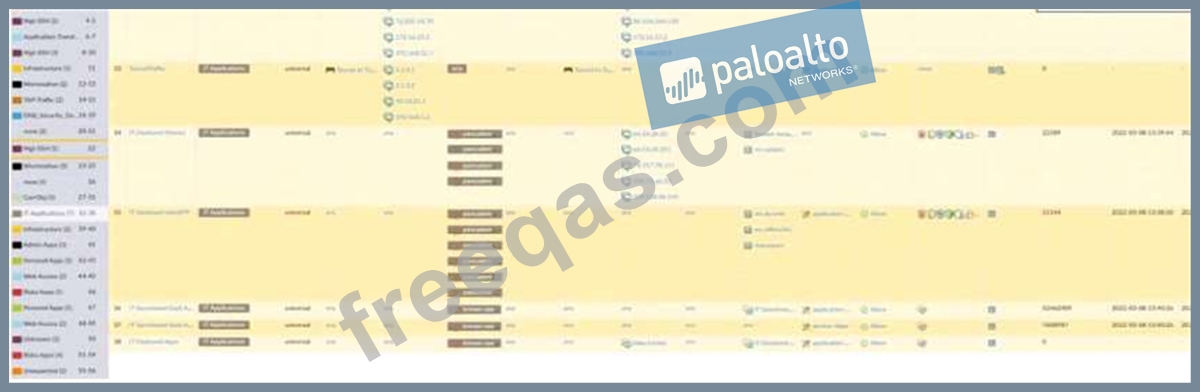
Enter your email address to download PaloAltoNetworks.PCNSA.v2023-02-15.q256 Dumps
