What must be configured for the firewall to access multiple authentication profiles for external services to authenticate a non-local account?
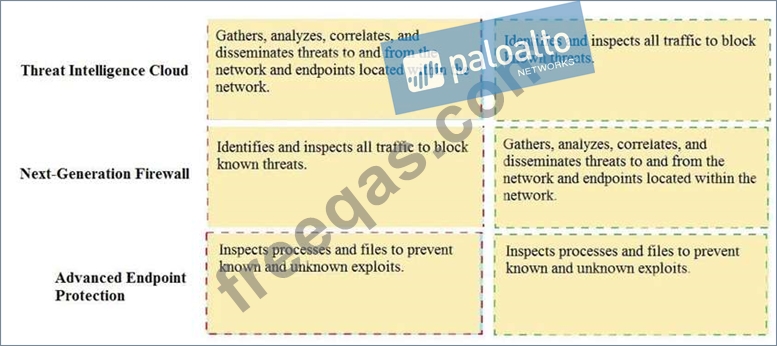
Match the Palo Alto Networks Security Operating Platform architecture to its description.
When creating a Source NAT policy, which entry in the Translated Packet tab will display the options Dynamic IP and Port, Dynamic, Static IP, and None?
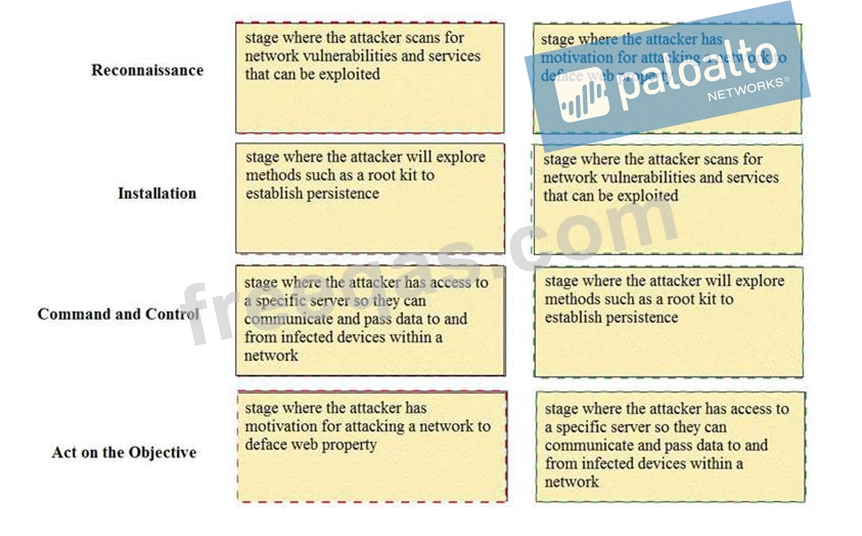
Match the Cyber-Attack Lifecycle stage to its correct description.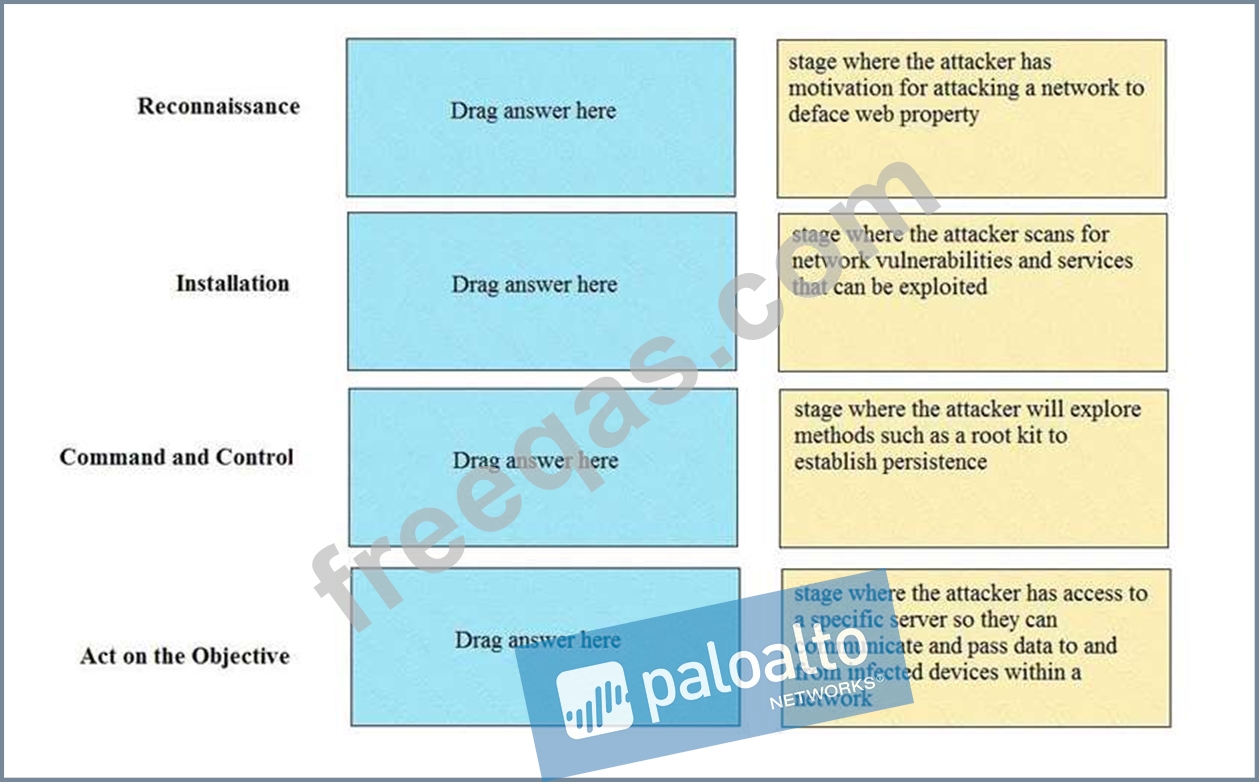
An administrator is investigating a log entry for a session that is allowed and has the end reason of aged-out. Which two fields could help in determining if this is normal? (Choose two.)
Enter your email address to download PaloAltoNetworks.PCNSA.v2023-02-15.q256 Dumps
