Given the topology, which zone type should zone A and zone B to be configured with?
Which Security profile must be added to Security policies to enable DNS Signatures to be checked?
What two authentication methods on the Palo Alto Networks firewalls support authentication and authorization for role-based access control? (Choose two.)
Which definition describes the guiding principle of the zero-trust architecture?
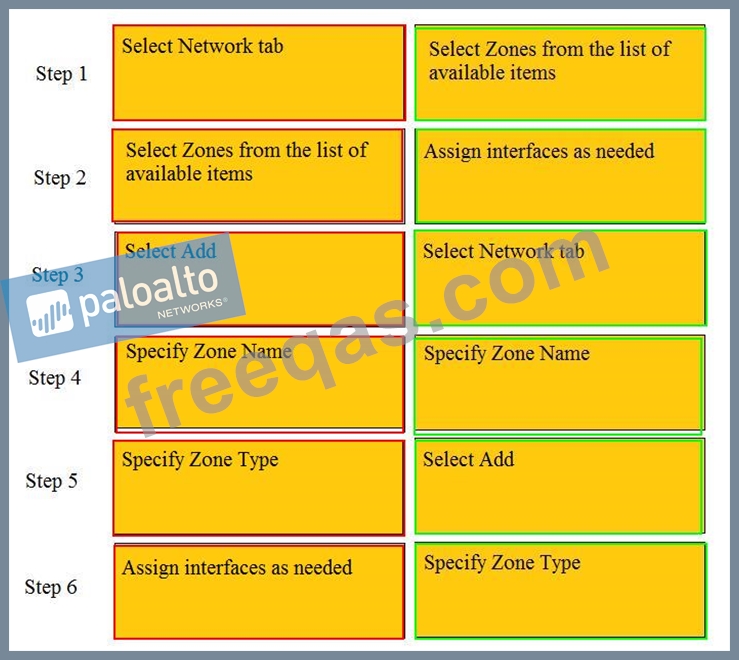
Order the steps needed to create a new security zone with a Palo Alto Networks firewall.
Step 1 - Select network tab
Step 2 - Select zones from the list of available items
Step 3 - Select Add
Step 4 - Specify Zone Name
Step 5 - Specify Zone Type
Step 6 - Assign interfaces as needed
Enter your email address to download PaloAltoNetworks.PCNSA.v2023-02-15.q256 Dumps
