Fill in the blank: The R80 SmartConsole, SmartEvent GUI client, and _______ consolidate billions of logs and shows them as prioritized security events.
The fw monitor utility is used to troubleshoot which of the following problems?
Which of the following is an identity acquisition method that allows a Security Gateway to identify Active Directory users and computers?
When you upload a package or license to the appropriate repository in SmartUpdate, where is the package or license stored
Examine the following Rule Base.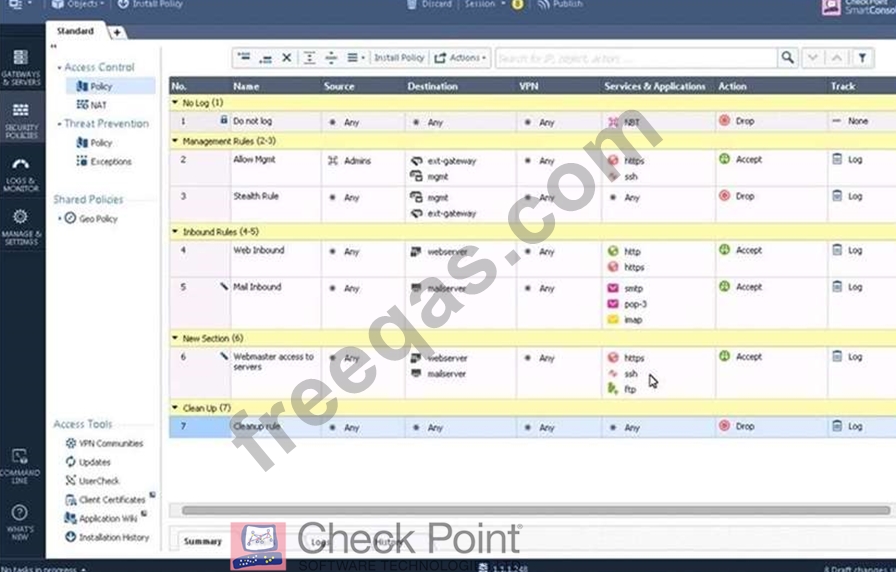
What can we infer about the recent changes made to the Rule Base?
Enter your email address to download CheckPoint.156-215.80.v2022-08-21.q419 Dumps
