In order to modify Security Policies the administrator can use which of the following tools? Select the BEST answer.
Which Threat Prevention Software Blade provides protection from malicious software that can infect your network computers?
Provide very wide coverage for all products and protocols, with noticeable performance impact.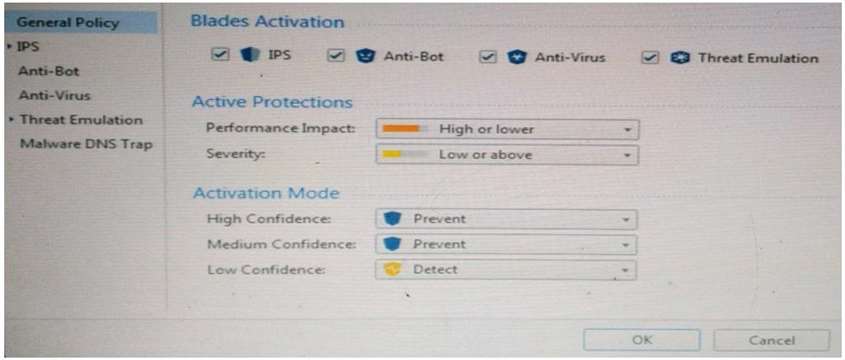
How could you tune the profile in order to lower the CPU load still maintaining security at good level? Select the BEST answer.
Which feature in R77 permits blocking specific IP addresses for a specified time period?
Enter your email address to download CheckPoint.156-215.81.v2022-09-24.q136 Dumps
