A security analyst detects an employee endpoint making connections to a malicious IP on the internet and downloaded a file named Test0511127691C.pdf. The analyst discovers the machine is infected by trojan malware. What must the analyst do to mitigate the threat using Cisco Secure Endpoint?
What must be automated to enhance the efficiency of a security team response?
What is a primary function of the Cisco Extended Detection and Response (XDR) solution?
An engineer configures trusted endpoints with Active Directory with Device Health to determine if an endpoint complies with the policy posture. After a week, an alert is received by one user, reporting problems accessing an application. When the engineer verifies the authentication report, this error is found:
"Endpoint is not trusted because Cisco Secure Endpoint check failed, Check user's endpoint in Cisco Secure Endpoint." Which action must the engineer take to permit access to the application again?
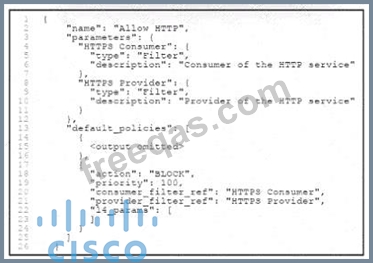
Refer to the exhibit. An engineer must create a segmentation policy in Cisco Secure Workload to block HTTP traffic. The indicated configuration was applied; however, HTTP traffic is still allowed. What should be done to meet the requirement?
