The main benefit of Cisco Secure Network Analytics in diagnosing access issues is its ability to:
The benefits of utilizing visibility and logging tools such as SIEM include:
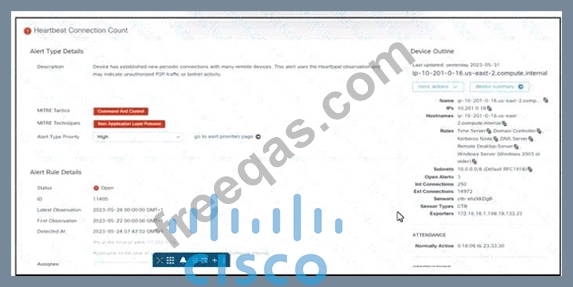
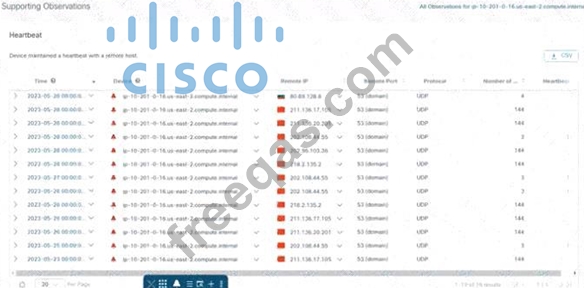
Refer to the exhibit. An engineer is investigating an unauthorized connection issue using Cisco Secure Cloud Analytics. Which two actions must be taken? (Choose two.)
After containing a cybersecurity threat, the next step is to _________ the damage or vulnerability to prevent future incidents.
