A penetration tester fuzzes an internal server looking for hidden services and applications and obtains the following output: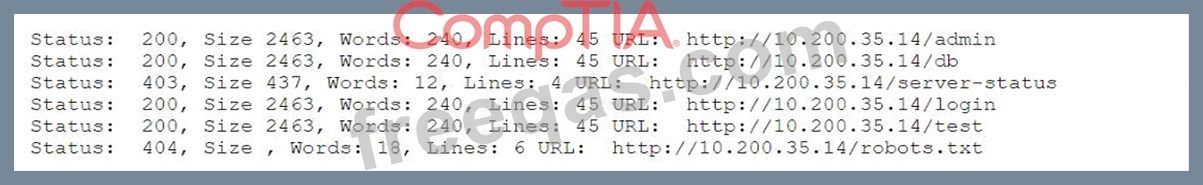
Which of the following is the most likely explanation for the output?
During a penetration-testing engagement, a consultant performs reconnaissance of a client to identify potential targets for a phishing campaign. Which of the following would allow the consultant to retrieve email addresses for technical and billing contacts quickly, without triggering any of the client's cybersecurity tools? (Choose two.)
A penetration tester conducted a discovery scan that generated the following: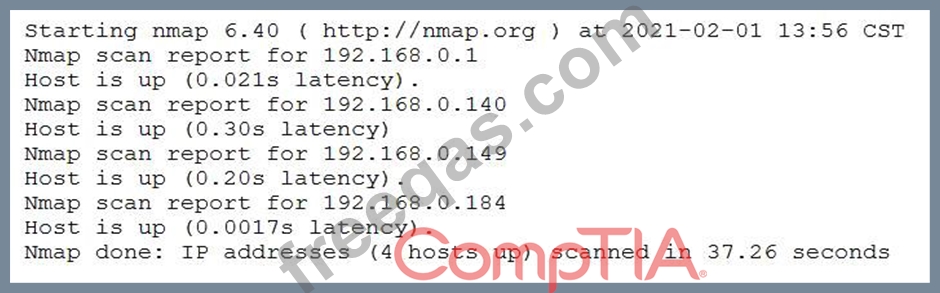
Which of the following commands generated the results above and will transform them into a list of active hosts for further analysis?
A penetration tester has prepared the following phishing email for an upcoming penetration test:
Which of the following is the penetration tester using MOST to influence phishing targets to click on the link?
A penetration tester managed to get control of an internal web server that is hosting the IT knowledge base. Which of the following attacks should the penetration tester attempt next?
