A business sector is highly competitive, and safeguarding trade secrets and critical information is paramount.
On a seasonal basis, an organization employs temporary hires and contractor personnel to accomplish its mission objectives. The temporary and contract personnel require access to network resources only when on the clock. Which of the following account management practices are the BEST ways to manage these accounts?
A security analyst captures forensic evidence from a potentially compromised system for further investigation. The evidence is documented and securely stored to FIRST:
During a recent security audit, an organization discovered that server configurations were changed without documented approval The investigators have confirmed that configuration changes require elevated permissions, and the investigation has failed to identify specific user accounts that are making the configuration changes Which of the following is MOST likely occurring''
A user suspects someone has been accessing a home network without permission by spoofing the MAC address of an authorized system. While attempting to determine if an authorized user is logged into the home network, the user reviews the wireless router, which shows the following table for systems that are currently on the home network.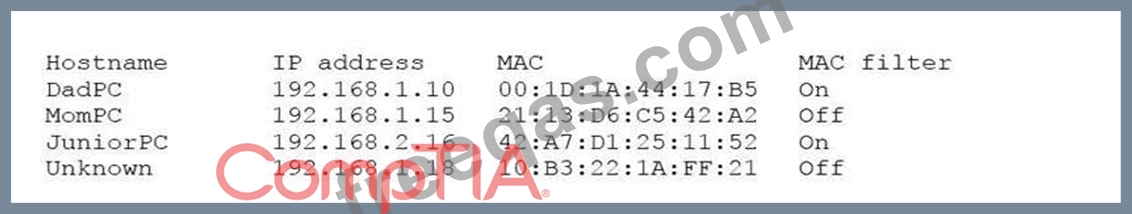
Which of the following should be the NEXT step to determine if there is an unauthorized user on the network?
A security engineer is configuring a system that requires the X.509 certificate information to be pasted into
a form field in Base64 encoded format to import it into the system. Which of the following certificate formats
should the engineer use to obtain the information in the required format?
