A system administrator is reviewing the following information from a compromised server.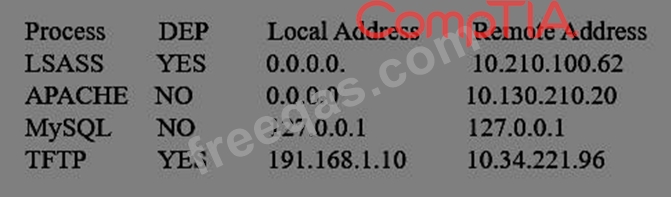
Given the above information, which of the following processes was MOST likely exploited via remote buffer overflow attack?
An employee in the finance department receives an email, which appears to come from the Chief Financial Officer (CFO), instructing the employee to immediately wire a large sum of money to a vendor. Which of the following BEST describes the principles of social engineering used? (Choose two.)
A system in the network is used to store proprietary secrets and needs the highest level of security possible.
Which of the following should a security administrator implement to ensure the system cannot be reached from the Internet?
A security engineer wants to further secure a sensitive VLAN on the network by introducing MFA. Which of the following is the BEST example of this?
A technician has been asked to document which services are running on each of a collection of 200 servers. Which of the following tools BEST meets this need while minimizing the work required?
