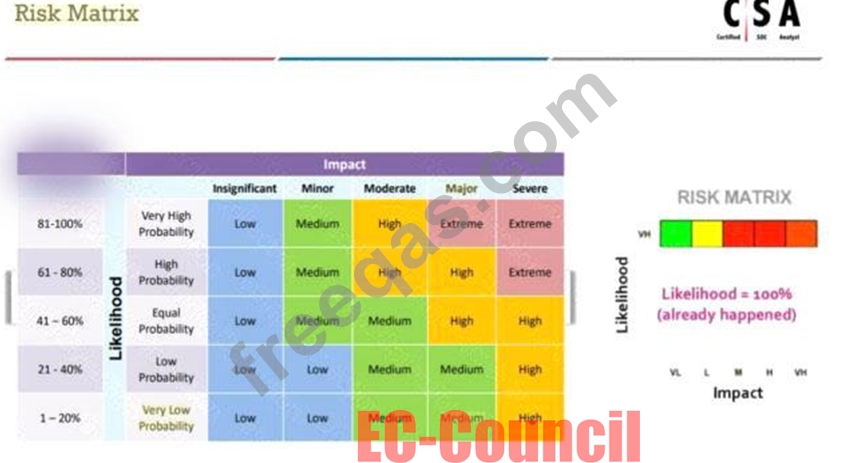
According to the Risk Matrix table, what will be the risk level when the probability of an attack is very low and the impact of that attack is major?
David is a SOC analyst in Karen Tech. One day an attack is initiated by the intruders but David was not able to find any suspicious events.
This type of incident is categorized into?

Which of the following service provides phishing protection and content filtering to manage the Internet experience on and off your network with the acceptable use or compliance policies?
Which of the following formula is used to calculate the EPS of the organization?

Which encoding replaces unusual ASCII characters with "%" followed by the character's two-digit ASCII code expressed in hexadecimal?
