A hard disk containing confidential data was damaged beyond repair. What should be done to the hard disk
to prevent access to the data residing on it?
During the development of an application, the quality assurance testing and user acceptance testing were combined. The MAJOR concern for an IS auditor reviewing the project is that there will be:
In the 2c area of the diagram, there are three hubs connected to each other. What potential risk might this indicate?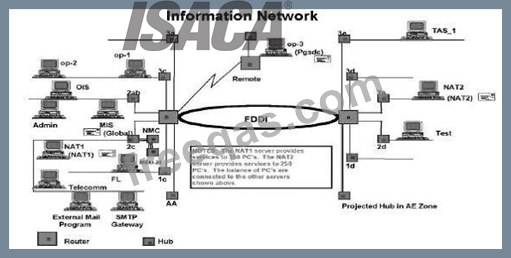
Which of the following is the BEST method to prevent wire transfer fraud by bank employees?
An IS auditor wants to determine who has oversight of staff performing a specific task and is referencing the organization's RACI chart. Which of the following roles within the chart would provide this information?
