Which data flow direction is protected in a zero trust firewall deployment that is not protected in a perimeter-only firewall deployment?
Actions can be set for which two items in a URL filtering security profile? (Choose two.)
Which Security policy match condition would an administrator use to block traffic from IP addresses on the Palo Alto Networks EDL of Known Malicious IP Addresses list?
Given the Cyber-Attack Lifecycle diagram, identify the stage in which the attacker can initiate malicious code against a targeted machine.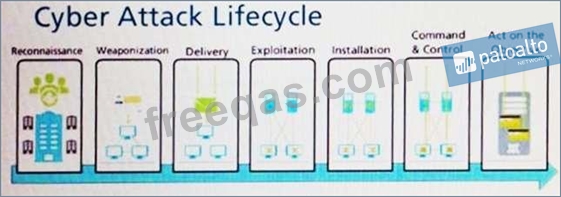
Which interface type is used to monitor traffic and cannot be used to perform traffic shaping?
Enter your email address to download PaloAltoNetworks.PCNSA.v2022-04-11.q158 Dumps
