Which file is used to save the running configuration with a Palo Alto Networks firewall?
Refer to the exhibit. An administrator is using DNAT to map two servers to a single public IP address. Traffic will be steered to the specific server based on the application, where Host A (10.1.1.100) receives HTTP traffic and Host B (10.1.1.101) receives SSH traffic.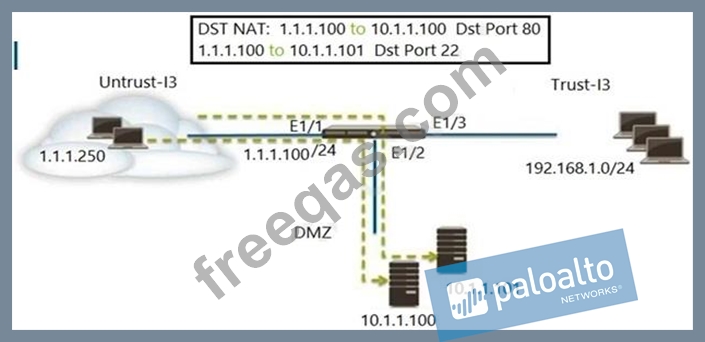
Which two Security policy rules will accomplish this configuration? (Choose two.)
Which information is included in device state other than the local configuration?
At which point in the app-ID update process can you determine if an existing policy rule is affected by an app-ID update?
Which five Zero Trust concepts does a Palo Alto Networks firewall apply to achieve an integrated approach to prevent threats? (Choose five.)
Enter your email address to download PaloAltoNetworks.PCNSA.v2022-04-11.q158 Dumps
