An administrator would like to use App-ID's deny action for an application and would like that action updated with dynamic updates as new content becomes available.
Which security policy action causes this?
Which protocol is used to map usernames to user groups when User-ID is configured?
The Port Mapping user mapping method can monitor which two types of environments? (Choose two.)
An administrator receives a global notification for a new malware that infects hosts. The infection will result in the infected host attempting to contact a command-and-control (C2) server. Which two security profile components will detect and prevent this threat after the firewall's signature database has been updated? (Choose two.)
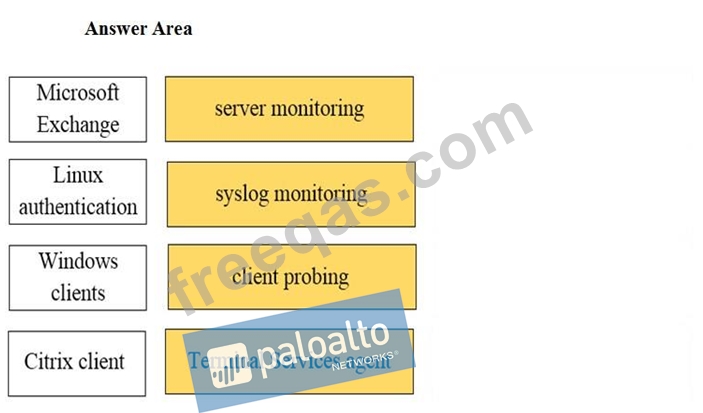
Drag and Drop Question
Match the network device with the correct User-ID technology.
Select and Place: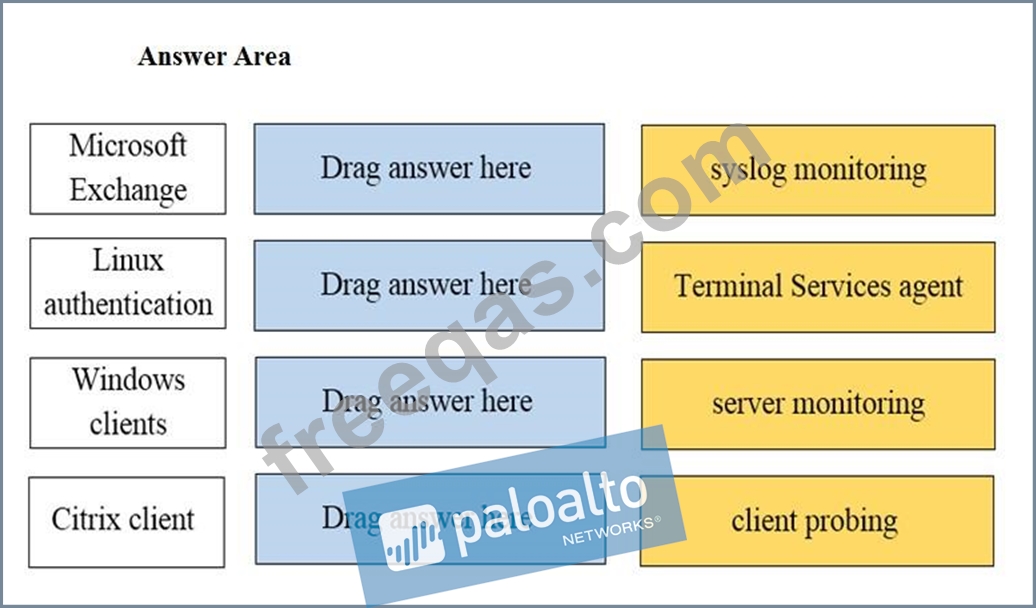
Enter your email address to download PaloAltoNetworks.PCNSA.v2023-02-15.q256 Dumps
