Which operations are allowed when working with App-ID application tags?
Assume that traffic matches a Security policy rule but the attached Security Profiles is configured to block matching traffic.
Which statement accurately describes how the firewall will apply an action to matching traffic?
Given the screenshot, what are two correct statements about the logged traffic? (Choose two.)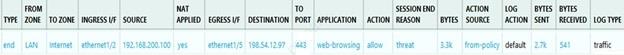
Based on the security policy rules shown, ssh will be allowed on which port?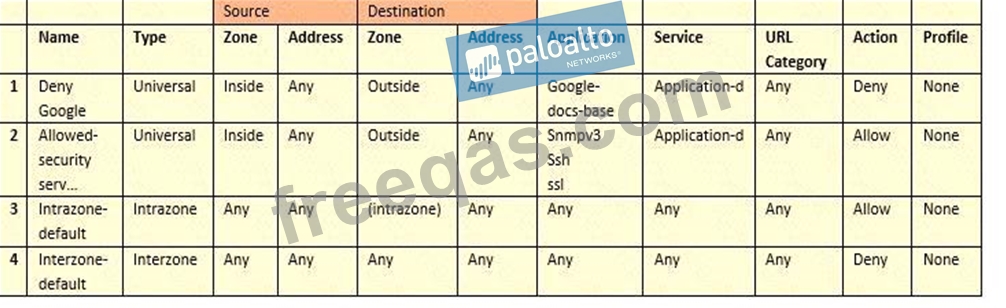
Enter your email address to download PaloAltoNetworks.PCNSA.v2023-02-15.q256 Dumps
