Given the Cyber-Attack Lifecycle diagram, identify the stage in which the attacker can initiate malicious code against a targeted machine.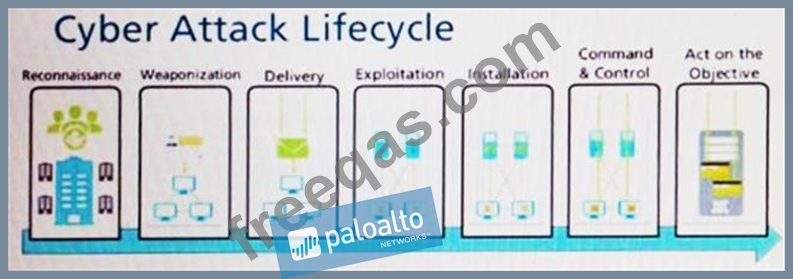
Given the image, which two options are true about the Security policy rules. (Choose two.)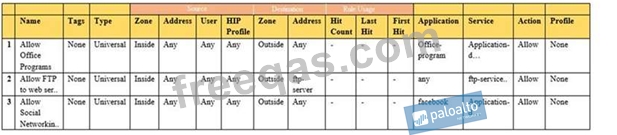
In a security policy what is the quickest way to rest all policy rule hit counters to zero?
An administrator needs to allow users to use their own office applications. How should the administrator configure the firewall to allow multiple applications in a dynamic environment?
An administrator is reviewing another administrator s Security policy log settings Which log setting configuration is consistent with best practices tor normal traffic?
Enter your email address to download PaloAltoNetworks.PCNSA.v2023-02-15.q256 Dumps
