What allows a security administrator to preview the Security policy rules that match new application signatures?
Based on the show security policy rule would match all FTP traffic from the inside zone to the outside zone?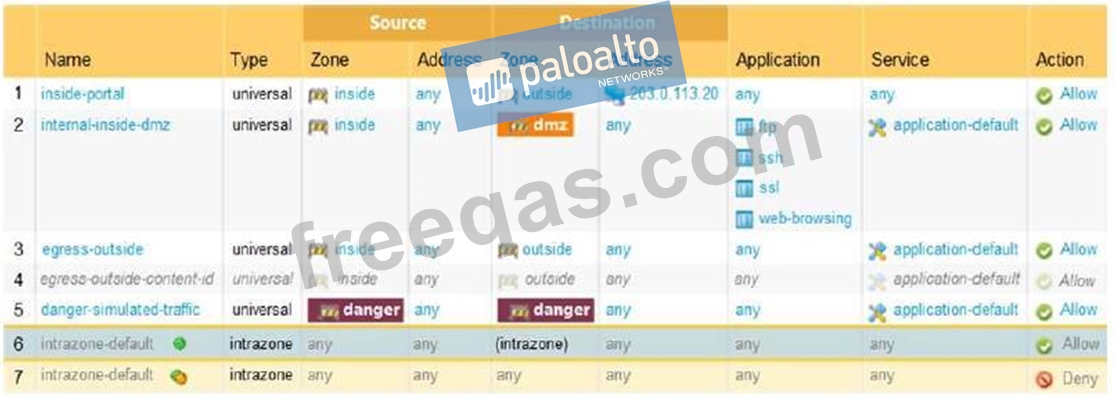
Drag and Drop Question
Match the Cyber-Attack Lifecycle stage to its correct description.
Select and Place: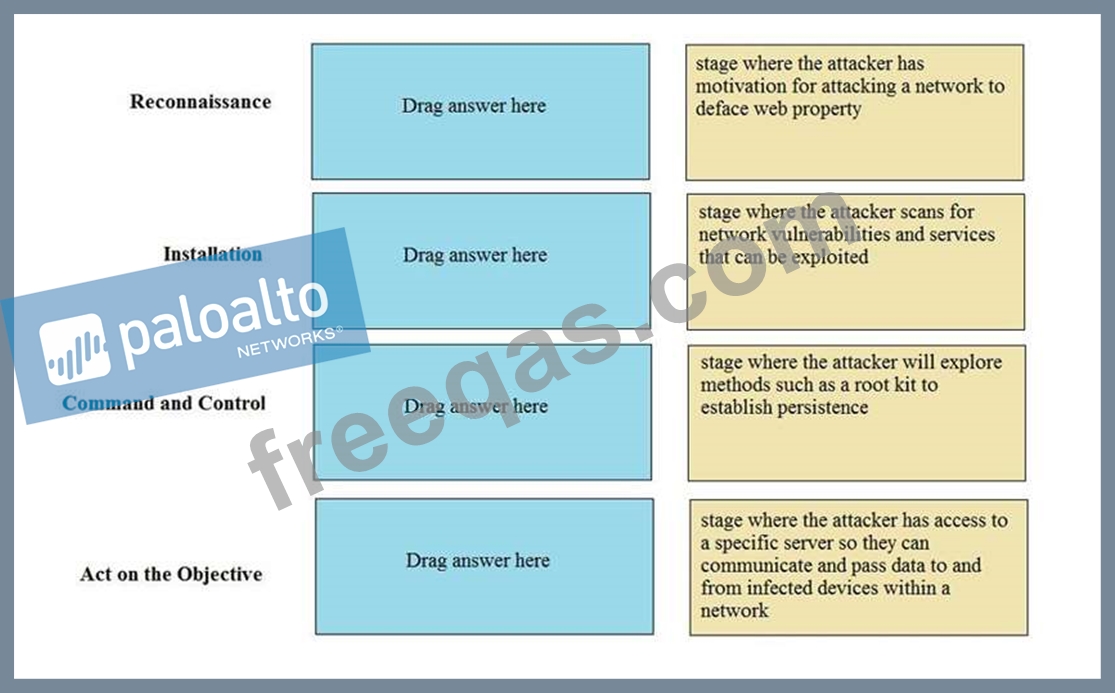

How many zones can an interface be assigned with a Palo Alto Networks firewall?
Enter your email address to download PaloAltoNetworks.PCNSA.v2023-02-15.q256 Dumps
