Multiple employees receive an email with a malicious attachment that begins to encrypt their hard drives and mapped shares on their devices when it is opened.
The network and security teams perform the following actions:
* Shut down all network shares.
* Run an email search identifying all employees who received the
malicious message.
* Reimage all devices belonging to users who opened the attachment.
Next, the teams want to re-enable the network shares. Which of the following BEST describes this phase of the incident response process?
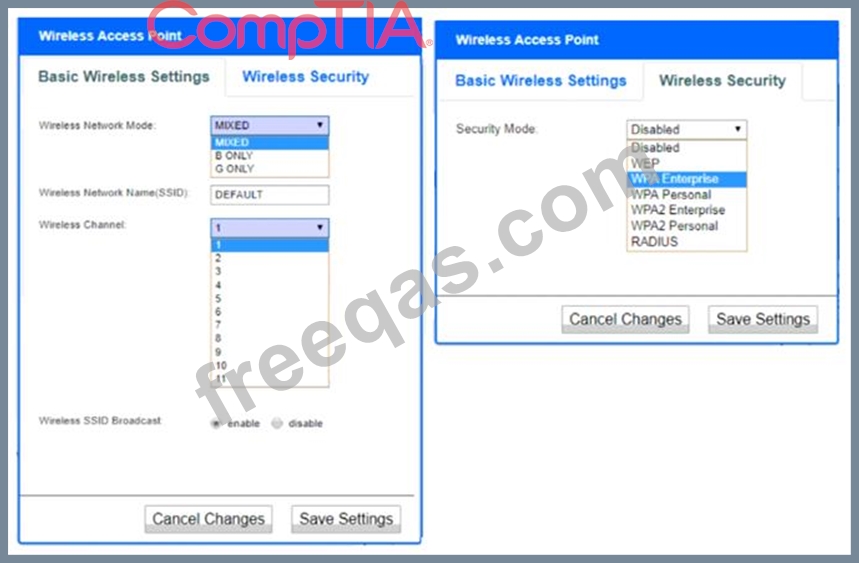
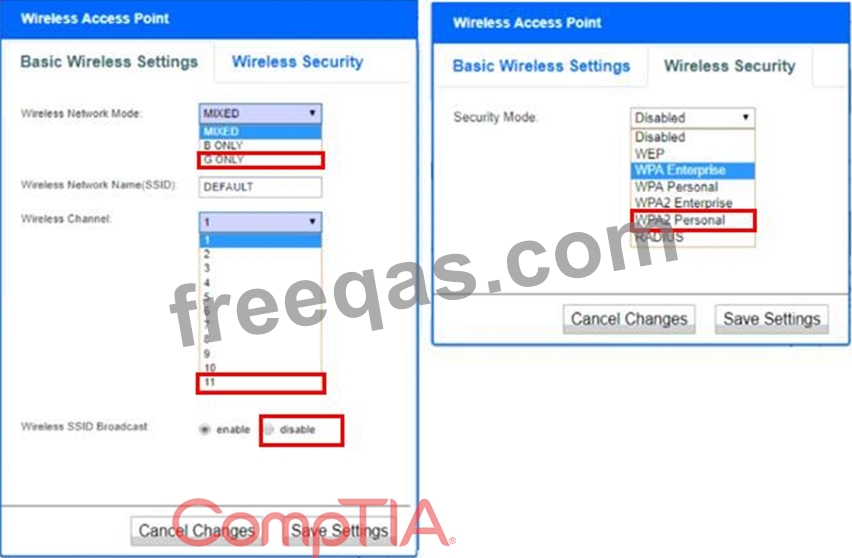
A newly purchased corporate WAP needs to be configured in the MOST secure manner possible.
INSTRUCTIONS
Please click on the below items on the network diagram and configure them accordingly:
* WAP
* DHCP Server
* AAA Server
* Wireless Controller
* LDAP Server
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.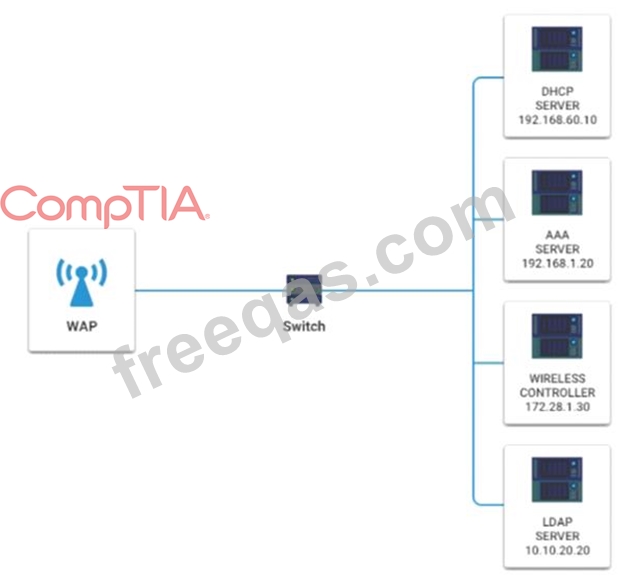
A company has noticed multiple instances of proprietary information on public websites. It has also observed an increase in the number of email messages sent to random employees containing malicious links and PDFs.
Which of the following changes should the company make to reduce the risks associated with phishing attacks? (Select TWO)
A product manager is concerned about continuing operations at a facility located in a region undergoing significant political unrest. After consulting with senior management, a decision is made to suspend operations at the facility until the situation stabilizes. Which of the following risk management strategies BEST describes management's response?
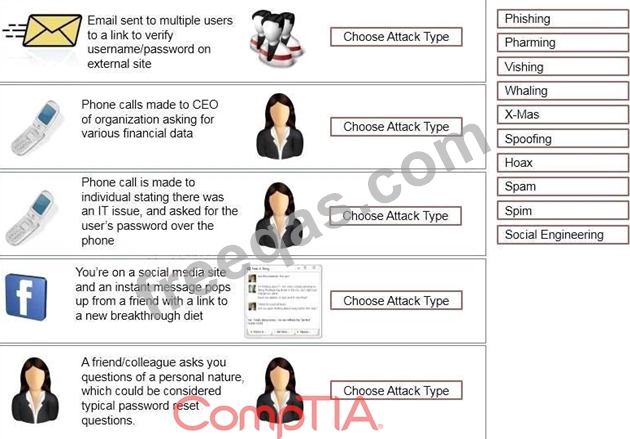
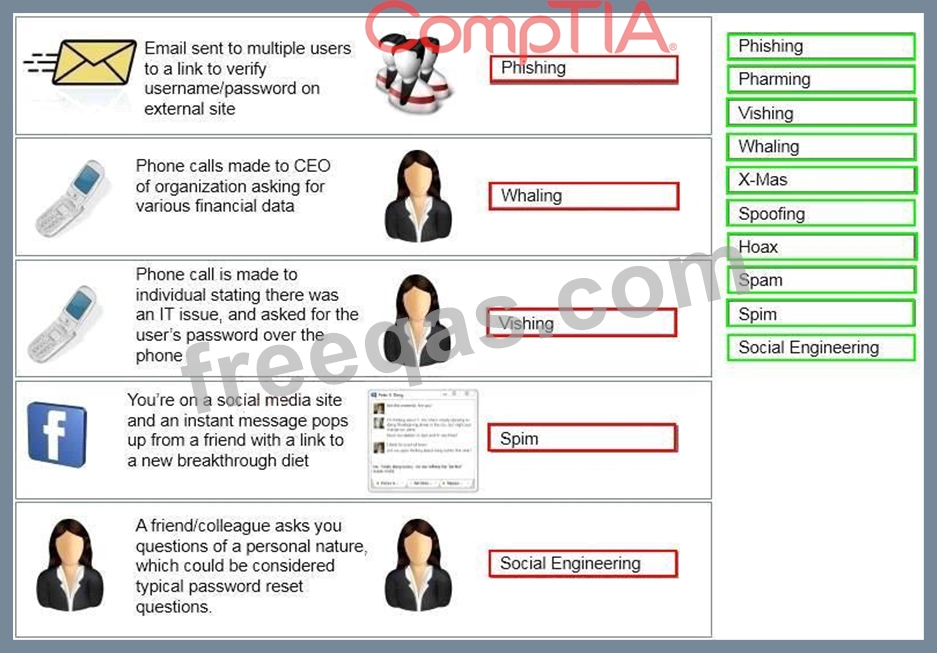
Task: Determine the types of attacks below by selecting an option from the dropdown list.