A company's user lockout policy is enabled after five unsuccessful login attempts. The help desk notices a user is repeatedly locked out over the course of a workweek. Upon contacting the user, the help desk discovers the user is on vacation and does not have network access. Which of the following types of attacks are MOST likely occurring? (Choose two.)
Joe, a contractor, is hired by a firm to perform a penetration test against the firm's infrastructure. While conducting the scan, he receives only the network diagram and the network list to scan against the network.
Which of the following scan types is Joe performing?
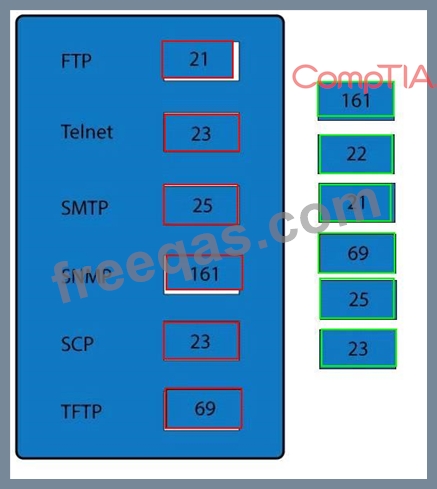
Drag and drop the correct protocol to its default port.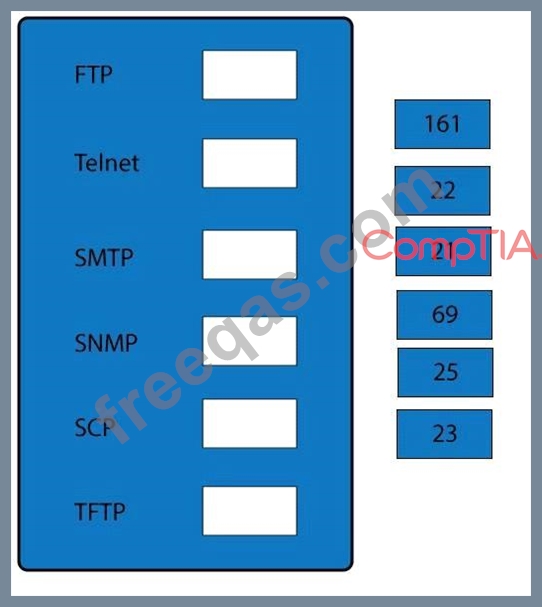
Staff members of an organization received an email message from the Chief Executive Officer (CEO) asking them for an urgent meeting in the main conference room. When the staff assembled, they learned the message received was not actually from the CEO. Which of the following BEST represents what happened?
A manager wants to distribute a report to several other managers within the company. Some of them reside in remote locations that are not connected to the domain but have a local server.
Because there is sensitive data within the report and the size is beyond the limit of the email attachment size, emailing the report is not an option.
Which of the following protocols should be implemented to distribute the report securely? (Select THREE)
