If two employees are encrypting traffic between them using a single encryption key, which of the following algorithms are they using?
A security analyst is reviewing the password policy for a service account that is used for a critical network service. The password policy for this account is as follows:
Which of the following adjustments would be the MOST appropriate for the service account?
Many employees are receiving email messages similar to the one shown below:
From IT department
To employee
Subject email quota exceeded
Pease click on the following link http:www.website.info/email.php?quota=1Gb and provide your username and password to increase your email quota. Upon reviewing other similar emails, the security administrator realized that all the phishing URLs have the following common elements; they all use HTTP, they all come from .info domains, and they all contain the same URI.
Which of the following should the security administrator configure on the corporate content filter to prevent users from accessing the phishing URL, while at the same time minimizing false positives?
A security analyst is testing both Windows and Linux systems for unauthorized DNS zone transfers within a LAN on comptia.org from example.org. Which of the following commands should the security analyst use? (Select two.) A: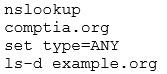
B: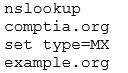
C: dig -axfr [email protected]
D: ipconfig/flushDNS
E:
F: [email protected] comptia.org
A security administrator is investigating a possible account compromise. The administrator logs onto a desktop computer, executes the command notepad.exe c:\Temp\qkakforlkgfkja.1og, and reviews the following:
Lee,\rI have completed the task that was assigned to me\rrespectfully\rJohn\r
https://www.portal.com\rjohnuser\rilovemycat2
Given the above output, which of the following is the MOST likely cause of this compromise?
