An organization was recently compromised by an attacker who used a server certificate with the company's domain issued by an irrefutable CA. Which of the following should be used to mitigate this risk in the future?
A penetration tester has written an application that performs a bit-by-bit XOR 0xFF operation on binaries
prior to transmission over untrusted media. Which of the following BEST describes the action performed by
this type of application?
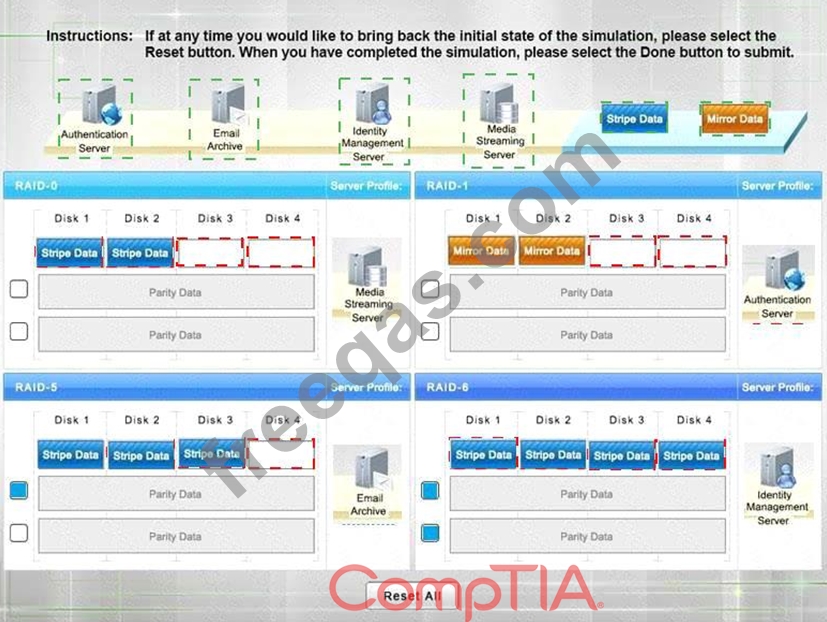
A security administrator is given the security and availability profiles for servers that are being deployed.
* Match each RAID type with the correct configuration and MINIMUM number of drives.
* Review the server profiles and match them with the appropriate RAID type based on integrity, availability, I/O, storage requirements. Instructions:
* All drive definitions can be dragged as many times as necessary
* Not all placeholders may be filled in the RAID configuration boxes
* If parity is required, please select the appropriate number of parity checkboxes
* Server profiles may be dragged only once
If at any time you would like to bring back the initial state of the simulation, please select the Reset button.
When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.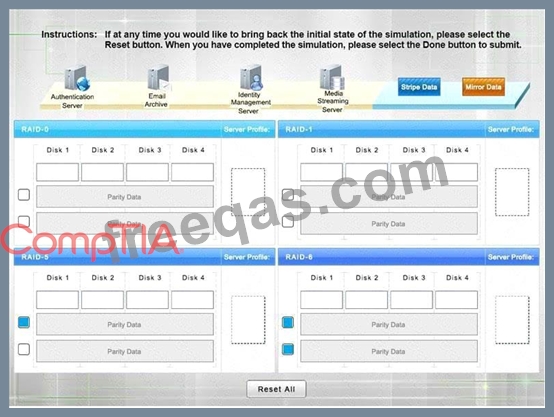

A security analyst runs a monthly file integrity check on the main web server. When analyzing the logs, the analyst observed the following entry: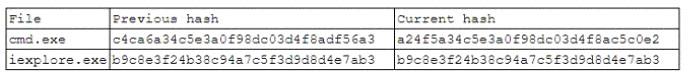
No OS patches were applied to this server during this period. Considering the log output, which of the following is the BEST conclusion?
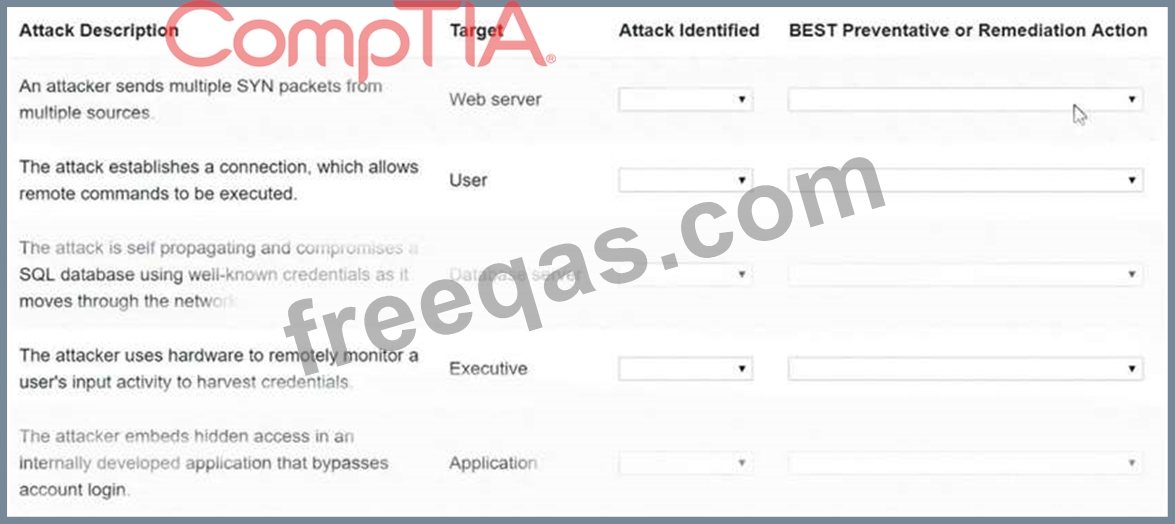
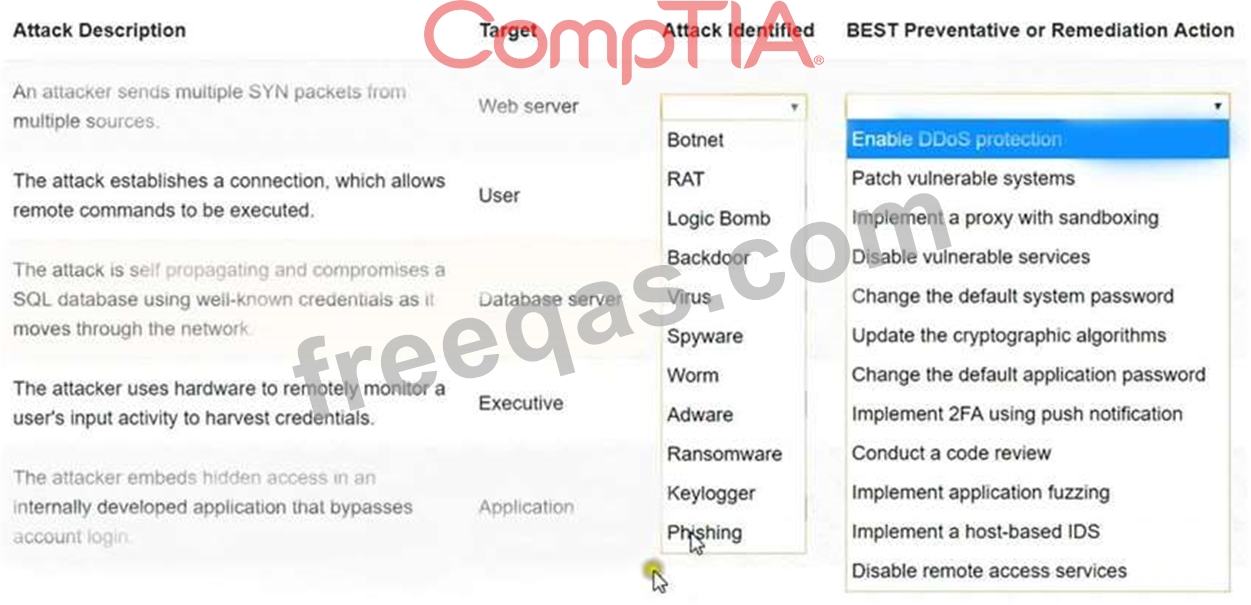
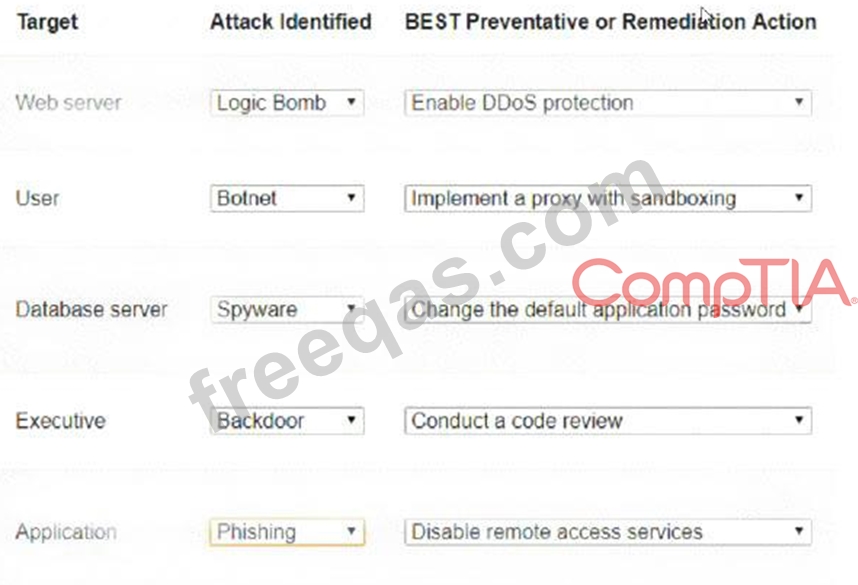
Select the appropriate attack and remediation from each drop-down list to label the corresponding attack with its remediation.
INSTRUCTIONS
Not all attacks and remediation actions will be used. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.