A software developer wants to ensure that the application is verifying that a key is valid before establishing SSL connections with random remote hosts on the Internet. Which of the following should be used in the code? (Select TWO.)
The Chief Security Officer (CSO) for an online retailer received a report from a penetration test that was performed against the company's servers. After reviewing the report, the CSO decided not to implement the recommended changes due to cost; instead, the CSO increased insurance coverage for data breaches. Which of the following describes how the CSO managed the risk?
To determine the ALE of a particular risk, which of the following must be calculated? (Select two.)
Multiple employees receive an email with a malicious attachment that begins to encrypt their hard drives and mapped shares on their devices when it is opened. The network and security teams perform the following actions:
Next, the teams want to re-enable the network shares. Which of the following BEST describes this phase of the incident response process?
An employee workstation with an IP address of 204.211.38.211/24 reports it is unable to submit print jobs to a network printer at 204.211.38.52/24 after a firewall upgrade. The active firewall rules are as follows: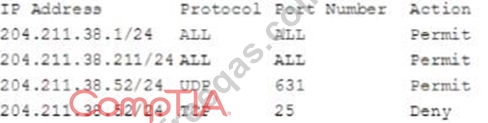
Assuming port numbers have not been changed from their defaults, which of the following should be modified to allow printing to the network printer?
