An attacker has obtained the user ID and password of a datacenter's backup operator and has gained access to a production system. Which of the following would be the attacker's NEXT action?
DRAG DROP
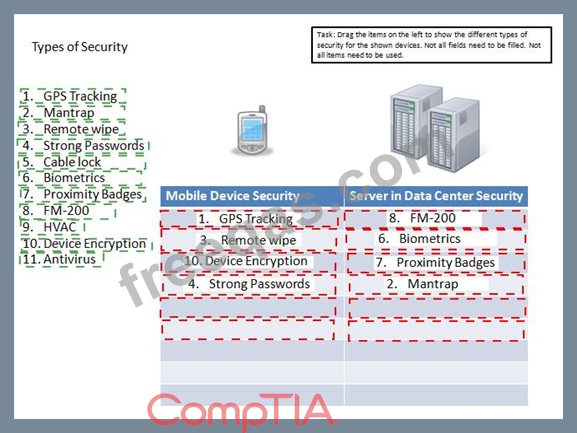
Drag the items on the left to show the different types of security for the shown devices.
Not all fields need to be filled. Not all items need to be used.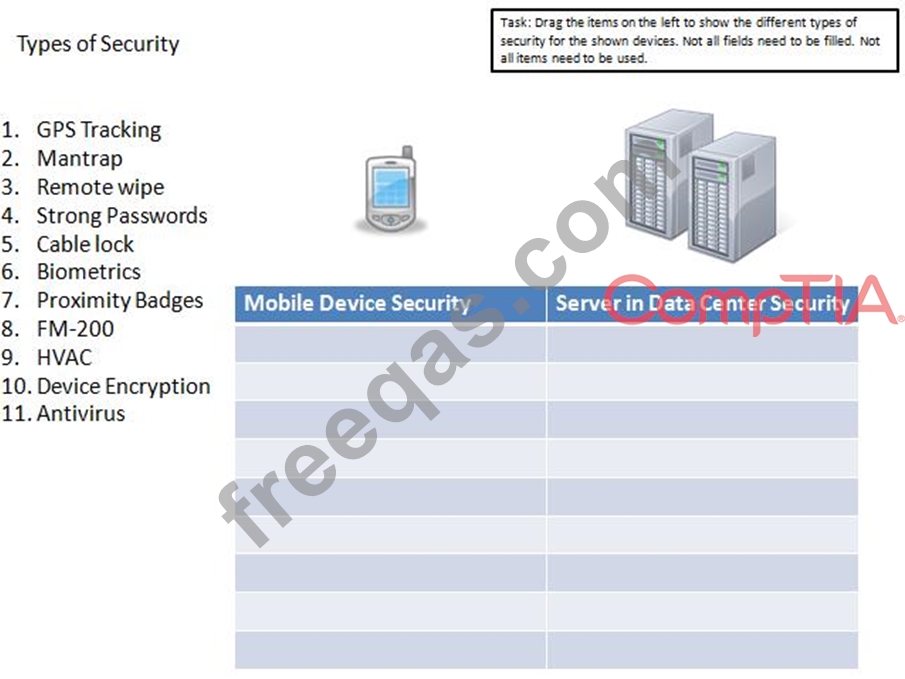
An organization plans to implement multifactor authentication techniques within the enterprise network
architecture. Each authentication factor is expected to be a unique control.
Which of the following BEST describes the proper employment of multifactor authentication?
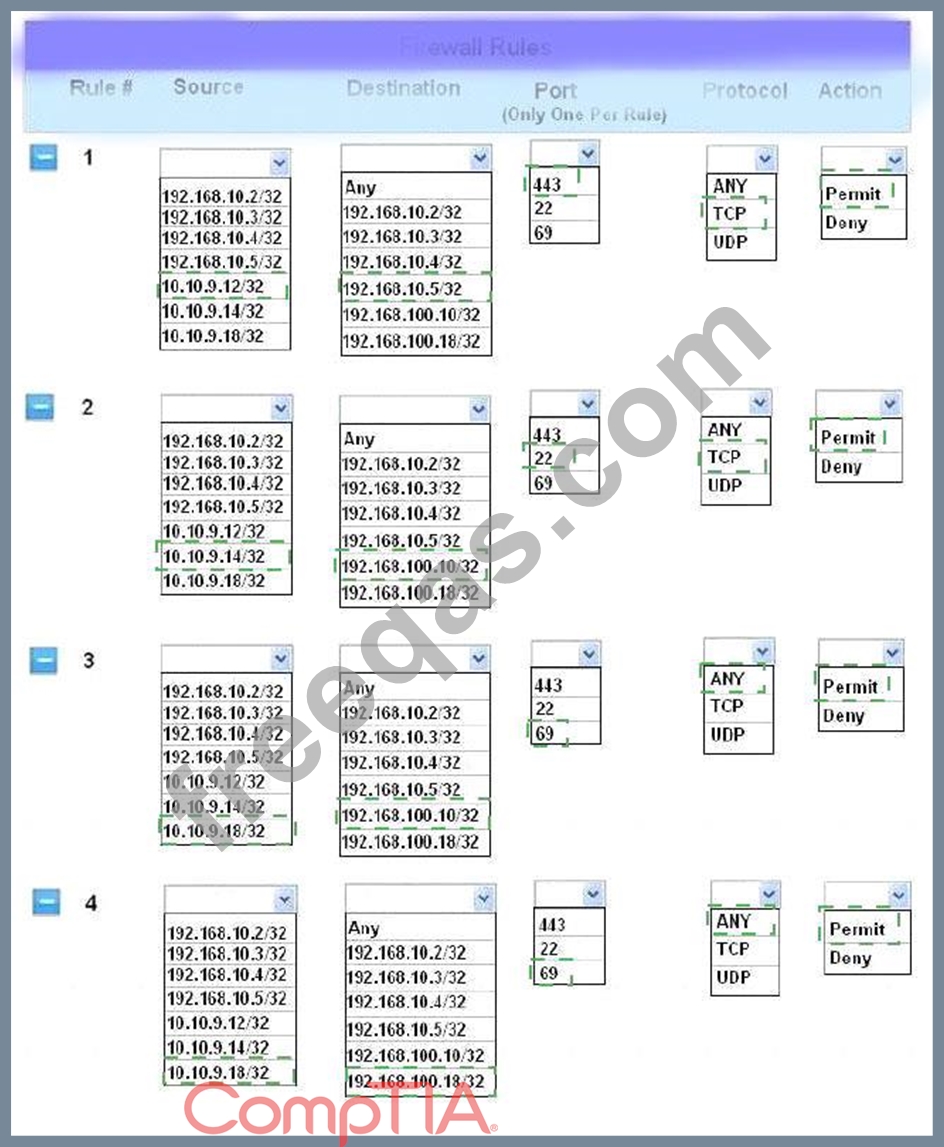
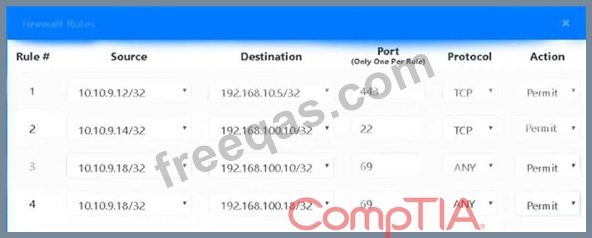
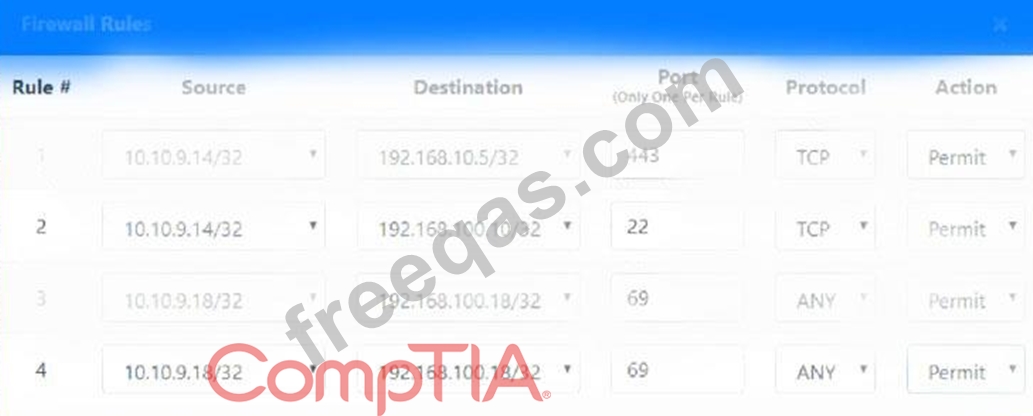
The security administrator has installed a new firewall which implements an implicit DENY policy by default.
INSTRUCTIONS:
Click on the firewall and configure it to allow ONLY the following communication.
1. The Accounting workstation can ONLY access the web server on the public network over the default HTTPS port. The accounting workstation should not access other networks.
2. The HR workstation should be restricted to communicate with the Financial server ONLY, over the default SCP port
3. The Admin workstation should ONLY be able to access the servers on the secure network over the default TFTP port.
Instructions: The firewall will process the rules in a top-down manner in order as a first match The port number must be typed in and only one port number can be entered per rule Type ANY for all ports. The original firewall configuration can be reset at any time by pressing the reset button. Once you have met the simulation requirements, click save and then Done to submit.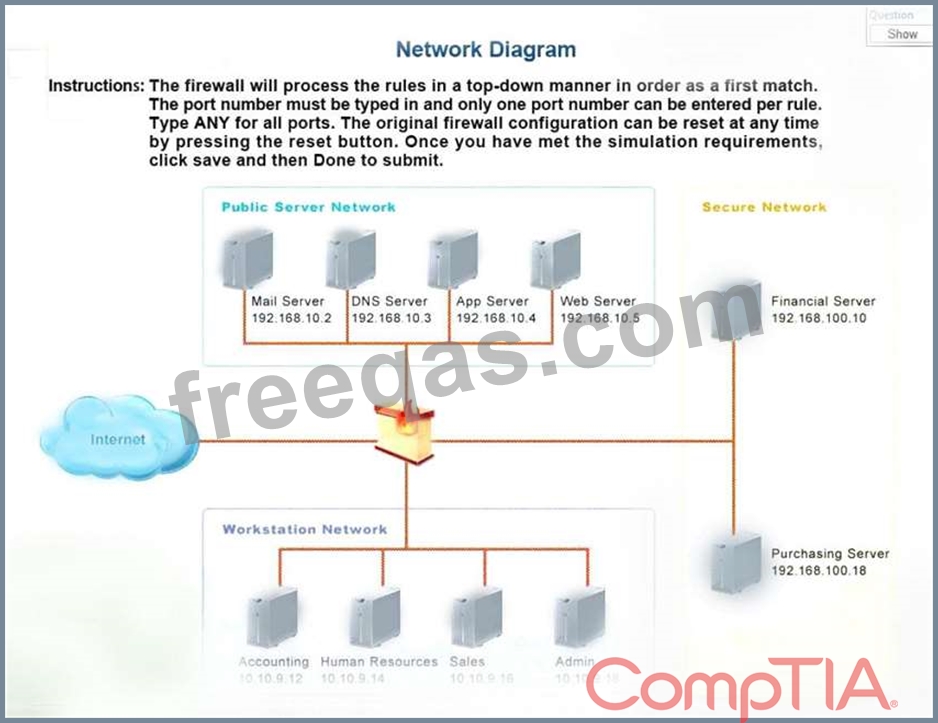
Hot Area: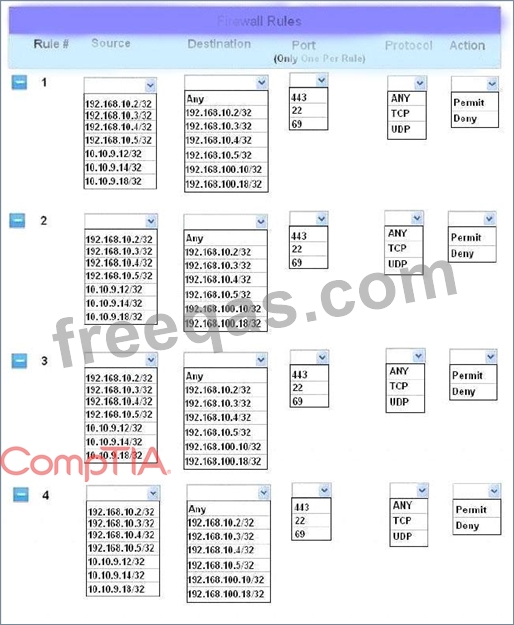
When performing data acquisition on a workstation, which of the following should be captured based on memory volatility? (Select two.)
