When conducting a penetration test, a pivot is used to describe a scenario in which
Which of the following identity access methods creates a cookie on the first logic to a central authority to allow logins to subsequent applications without referring credentials?
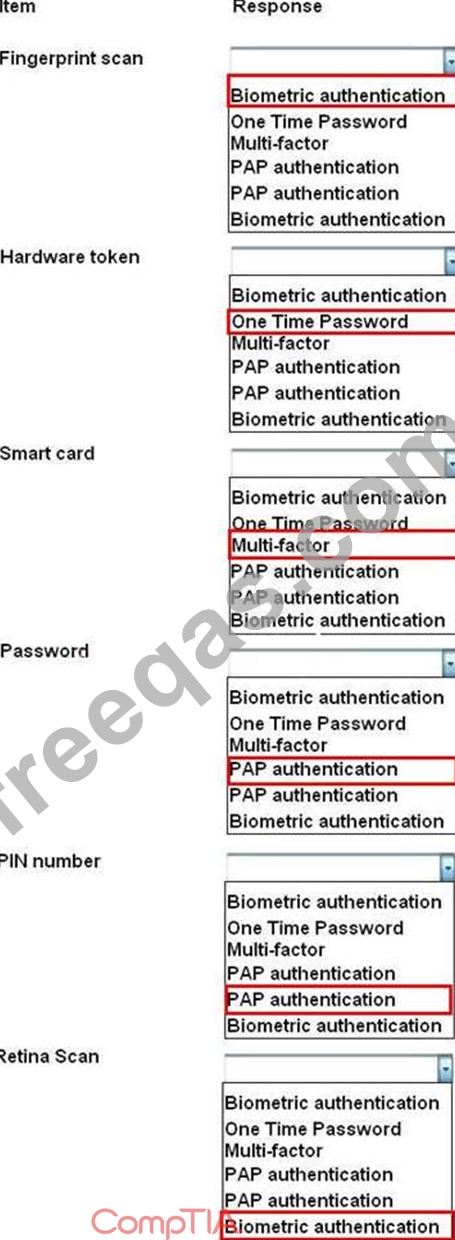
For each of the given items, select the appropriate authentication category from the drop down choices.
Select the appropriate authentication type for the following items: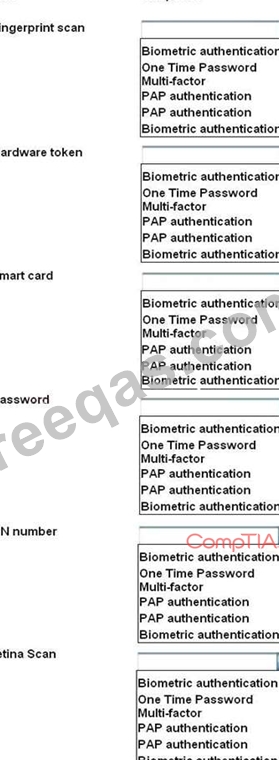
A security administrator is given the security and availability profiles for servers that are being deployed.
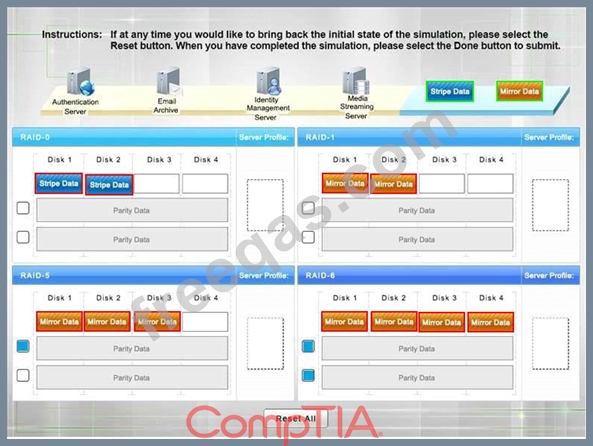
Match each RAID type with the correct configuration and MINIMUM number of drives.
Review the server profiles and match them with the appropriate RAID type based on integrity, availability, I/O, storage requirements. Instructions:
All drive definitions can be dragged as many times as necessary
Not all placeholders may be filled in the RAID configuration boxes
If parity is required, please select the appropriate number of parity checkboxes Server profiles may be dragged only once If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.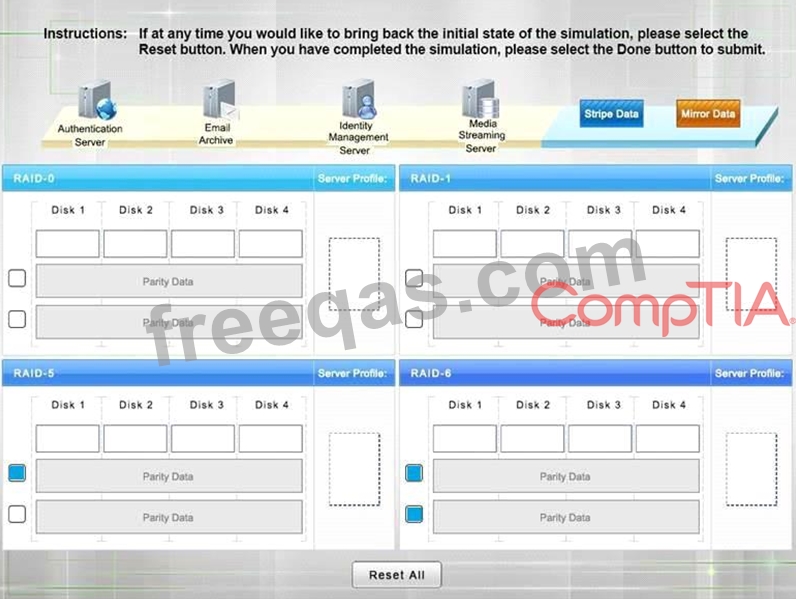
In terms of encrypting data, which of the following is BEST described as a way to safeguard password data by adding random data to it in storage?
