A company was recently audited by a third party. The audit revealed the company's network devices were transferring files in the clear.
Which of the following protocols should the company use to transfer files?
An auditor is reviewing the following output from a password-cracking tool: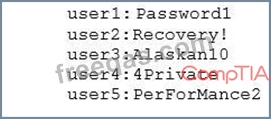
Which of the following methods did the auditor MOST likely use?
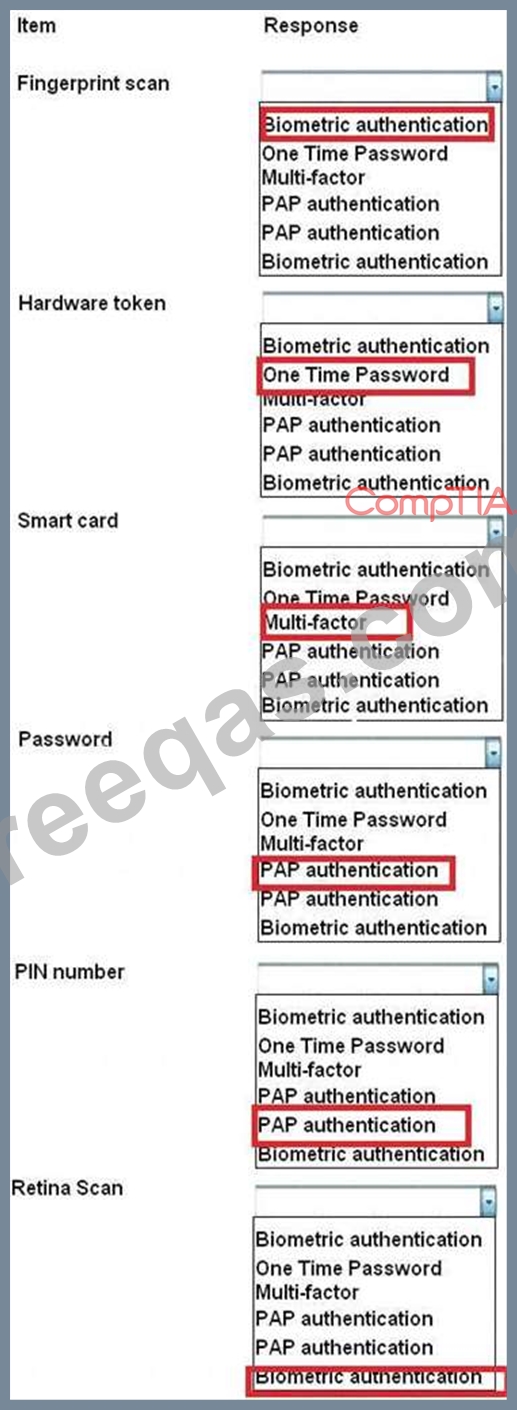
For each of the given items, select the appropriate authentication category from the drop down choices.
Select the appropriate authentication type for the following items:

A security manager is preparing the training portion of an incident plan. Which of the following job roles should receive training on forensics, chain of custody, and the order of volatility?
A security technician would like to obscure sensitive data within a file so that it can be transferred without causing suspicion.
Which of the following technologies would BEST be suited to accomplish this?
